Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Paths to Power in Active Directory Part 2: ESC1 – No One, Yet Anyone
This is the second post in this series. Part I can be found here.
Continue Reading
Extract Secrets from Multiple Configuration Files Using Vim
You're SSH'd into a compromised Linux server during a penetration test. You've found the ...
Continue Reading
Paths to Power in Active Directory Part 1: How AD CS Misconfigurations Become the Keys to the Kingdom
An Introduction to Active Directory Certificate Services (AD CS) I am still pretty new to ...
Continue Reading
No Broadcast Traffic? No Problem! - NetExec SMB Slinky Module
As pentesters, tools such as Responder and Ntlmrelayx are great tools for capturing hashes or ...
Continue Reading
Annual Pentests Aren't Cutting It Anymore: Why Continuous Testing Beats Scrambling at Renewal Time
Let's be honest about something: if you're still relying on that once-a-year penetration test to ...
Continue Reading
Quantum Leaping Through Data: Preparing for the Quantum Encryption Transition
best practices |
compliance |
risk assessment |
NIST |
CISA
Quantum computing and its implications for cryptography isn't a new discussion. Security ...
Continue Reading
Your Risk Framework Is Broken: The Al Reality Check Every CISO Needs
Every risk management framework in cybersecurity relies on the same fundamental equation: Risk = ...
Continue Reading
Rolling for Resilience Part 2: The Communication Gauntlet
This is the second post in this series addressing my perspective on the current state of ...
Continue Reading
Bypassing Browser PDF Security: Using Embedded JavaScript Forms for Social Engineering
I can say that, since I started my journey at Secure Ideas, I’ve felt extremely fortunate. Not only ...
Continue Reading
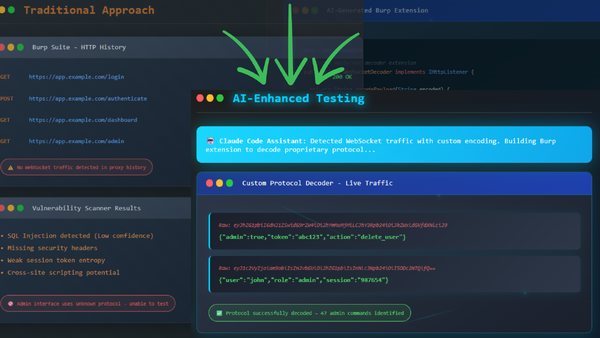
The Real AI Revolution in Penetration Testing
Custom Tooling at Lightning Speed Most cybersecurity professionals hear "AI in penetration testing" ...
Continue Reading
Quick Bites 13 – Network Pentest Restrictions Can Hurt Your Business
Too Many Network Pentest Restrictions Can Hurt Your Business
Continue Reading
But AI Can Give Me the Commands! Why You Still Need to Learn the Linux File System
Linux |
AI |
AI Security
It’s now easier than ever for AI to write your bash scripts or give you the exact command to ...
Continue Reading
Secure Password Management in PowerShell: Best Practices
When working with PowerShell to automate tasks, managing credentials securely is a critical ...
Continue Reading
Rolling for Resilience: A Strategic Guide to Cybersecurity Table-top Exercises
This is the first post in this series addressing my perspective on the current state of ...
Continue Reading
Risk-Driven Approach: The Federal Government’s Shift in Cybersecurity Burden
From All-Hazards to Risk-Informed The New Risk-Informed Paradigm One of the most significant shifts ...
Continue Reading
Understanding Garbage Findings
There is a well-meaning desire among penetration testers to produce findings. The fact of the ...
Continue Reading
Houston, We Have a Problem
Satellite Security Testing: A Holistic Approach Last month, I had the opportunity to present at ...
Continue Reading
Cybersecurity Essentials for SMBs: Building a Robust Program
When discussions arise around companies' cybersecurity programs, the focus often gravitates towards ...
Continue Reading
The Essential Eight
NIST |
Essential 8 |
ASD
Australian Signals Directorate’s Top 8 Controls to Mitigate Cyber Security Incidents & How They ...
Continue Reading
From Nmap to CSV
How Experience and Management Skills Improve Data Analysis for Security Professionals The other ...
Continue Reading
You Don’t Need PKINIT To Win It
Privilege Escalation using LDAP Part 1 Pass-the-certificate has become a common method used by ...
Continue Reading
Built-In Network Capture with Windows 11
Did you know that Windows has a built-in network packet capture utility? And that it isn’t even GUI ...
Continue Reading
Running and Debugging Non-native ELF Binaries Locally Using QEMU, BINFMT, and GDB
Overview One of the common tasks that occurs when pentesting an embedded device is binary analysis ...
Continue Reading
Who Really Owns Your Data?
When we traded ownership for convenience, we never imagined that everything from our books to our ...
Continue Reading
When Algorithms Aren’t Enough: Why the Human Element Still Matters in Modern Penetration Testing
The cybersecurity industry has evolved into two distinct approaches when it comes to penetration ...
Continue Reading
OT: The Invisible World in Motion
We are surrounded by technology, not just in what we carry but in nearly every aspect of our daily ...
Continue Reading
Solicited Public Comment on HIPAA Security Rule NPRM To Strengthen the Cybersecurity of ePHI
The Department of Health and Human Services (HHS) wants to raise the benchmarks of the Security ...
Continue Reading
Building a Custom Burp Suite Collaborator Everywhere BApp
Have you ever run into an issue when using a BApp in Burp Suite that it didn’t quite work with your ...
Continue Reading
Quick Bites Episode 12 - Hidden Treasures
Ever go on a treasure hunt? Ever find any hidden treasure? It’s a blast! One of my favorite ...
Continue Reading
Operational Technology’s use of Wireless Networks
The Growing Importance and Challenges of Wireless Networks in Operational Technology
Continue Reading
When Security Fails: What The DeepSeek Incident Can Teach Us About AI Security
The advent of generative AI - particularly Large Language Models (LLMs) - marks a paradigm shift in ...
Continue Reading
Navigating the Security Roadmap: TISAX for Automotive OEMs
As an Original Equipment Manufacturer, you stand at the helm of automotive innovation. Your ...
Continue Reading
Countdown to Full Compliance: PCI-DSS 4.0.1
As the deadline for full compliance with PCI DSS v4.0.1 approaches, organizations should be turning ...
Continue Reading
Best Practices and Risks Considerations in Automation like LCNC and RPA
best practices |
LCNC |
RPA
The Rise of Low-Code/No-Code and RPA in Digital Transformation Technologies such as ...
Continue Reading
Understanding TISAX: Securing the Path Forward for Automotive Innovation
The automotive industry's digital transformation has created unprecedented security challenges ...
Continue Reading
The Critical Need for API Security Testing
Application security penetration tests once were a novelty, a luxury that only organizations with ...
Continue Reading
Stay safe from cybercrime with these five tips
Cybercriminals will use every tactic in the book to steal data, drain bank accounts, and extort ...
Continue Reading
The Fellowship of the Phish: PayPal's Perilous Request Feature
In cybersecurity, we often find ourselves fixated on the latest sophisticated malware or zero-day ...
Continue Reading
Secure Ideas is CREST-Certified. Here’s Why That Matters
Cybersecurity is no longer a monolithic topic – if it ever was. Specialization matters. ...
Continue Reading
Step Into the Shadows: The Haunting of the Dark Web
Ready to venture into the unseen corners of the internet? Join us for a Halloween webcast, "The ...
Continue Reading
Automating UART Command Injection with the Flipper Zero and JavaScript
Overview The Flipper Zero recently came out with a JavaScript system built off of MJS that exposes ...
Continue Reading
What’s new in the OWASP Proactive Controls for 2024
I have taught a number of application security classes to developers. When it comes to ...
Continue Reading
Many Hands Approach To AppSec
"If you want to frustrate a good developer, interfere with their ability to complete work." - ...
Continue Reading
The CISO's Myopia
Fifteen years ago, I wrote an article entitled "The CSO’s Myopia." At the time, I aimed to ...
Continue Reading
Kubernetes Pentesting: The Hacker’s Harvest
Are you ready to dive into the world of Kubernetes pentesting? Join us for our upcoming webcast, ...
Continue Reading
From Code to Cloud: Strengthening IaC Security with SAST
Infrastructure as Code (IaC) is a cornerstone in modern DevOps and DevSecOps practices, but how do ...
Continue Reading
NMAP in Action: API's
In a recent blog post, my coworker Josh introduced the fundamentals of NMAP and highlighted its ...
Continue Reading
Tartar Sauce for your Phishing Program
Phishing awareness exercises have become a common part of the larger security strategy for many ...
Continue Reading
From Linux to PowerShell and Back: A Quick Command Reference
Quick Overview If you are like me, you are switching back and forth between Linux and Windows ...
Continue Reading
Flipper Zero: Hardware Hacking JTAG and SWD Webcast
The Flipper Zero is known as a hacking multitool. It can cover a range of hacking from sub-ghz ...
Continue Reading
The Client-Side Security Trap: A Warning For Developers
application security |
SDLC |
framework |
Secure Development |
Software Development |
Secure Coding Practices |
client-side Security |
Content Security Policy |
Lifecycle |
Front-End Security
Considering the inherent complexities of modern web development, understanding the distinct roles ...
Continue Reading
Top 5 Security Considerations for a New Web App: 5. Establishing a Dependency Patching Plan
Welcome to our comprehensive series on the Top 5 Security Considerations for a New Web App. This ...
Continue Reading
Top 5 Security Considerations for a New Web App: 4. Logging & Monitoring
Welcome to our comprehensive series on the Top 5 Security Considerations for a New Web App. This ...
Continue Reading
Top 5 Security Considerations for a New Web App: 3. Data Encryption & Protection
Welcome to my comprehensive series on the Top 5 Security Considerations for a New Web App. This ...
Continue Reading
Top 5 Security Considerations for a New Web App: 2. Authentication & Authorization
Welcome to my comprehensive series on the Top 5 Security Considerations for a New Web App. This ...
Continue Reading
Top 5 Security Considerations for a New Web App: 1. Secure Coding
Welcome to my comprehensive series on the Top 5 Security Considerations for a New Web App. For this ...
Continue Reading
Top 5 Security Considerations for a New Web App
There was a time when many folks responsible for building and deploying web applications were naive ...
Continue Reading
Quick Bites Episode 11 – Ranking Application Risks
application security |
hacking |
pentesting |
Quick Bites |
risk assessment |
appsec |
application risk |
ranking risk
Threats often evolve faster than defenders can figure out how to prevent them. That’s why keeping ...
Continue Reading
SQL Injection Vulnerability: Identification and Prevention Methods
Recently, the FBI and CISA released a Secure by Design alert calling for the elimination of SQL ...
Continue Reading
Being Safe and Secure with Cross-Origin Messaging
security |
JavaScript |
application |
web |
cross-origin
Complex web and mobile apps often depend on cross-domain interactions between different online ...
Continue Reading
Prompt Injection
information security |
AI |
machine learning |
artificial intelligence |
cyber security |
Prompt Engineering |
AI Security |
Prompt Injection |
ML
What is Prompt Injection?
Continue Reading
Quick Bites Episode 10 – Half Shells and Full Shells
hacking |
pentesting |
shell |
Quick Bites |
reverse shells |
terminal |
python |
python3 |
netcat |
command line |
nc
I wanted to share a really cool technique that I found out about recently. Now I will say this is ...
Continue Reading
Intro to NMAP
My journey into cybersecurity has been anything but easy. This field offers a wide range of ...
Continue Reading
What does PCI require for Developer Training?
Training |
PCI |
developers |
application security |
appsec
The Payment Card Industry Security Standards Council (PCI SSC) defines compliance standards for all ...
Continue Reading
Mitigating Exploitation Risks in Active Directory Certificate Services
A recent pentest of an Active Directory environment turned into a struggle to uncover an avenue for ...
Continue Reading
Uncharted Waters: Network Depths with runZero & OPNsense
network security |
Vagrant |
runZero |
homelab |
Series: Uncharted Waters |
OPNSense |
asset discovery
(artwork created by stable diffusion)
Continue Reading
Everything You Need To Know About The Nist Cybersecurity Framework 2.0
best practices |
cybersecurity |
government |
CSF |
cybersecurity standards |
framework |
NIST |
profiles |
tiers
This week NIST released the highly anticipated update to the Cybersecurity Framework (CSF). Here’s ...
Continue Reading
Quick Bites 9 – Adventuring into the Unknown: The Hacker Subculture
One of the really cool things about being a hacker is that we get to discover new things. It’s kind ...
Continue Reading
Mobile Testing Considerations
penetration testing |
Secure Ideas |
cyber security |
mobile application security testing |
mobile app penetration testing |
mobile application development |
mobile application testing |
testing mobile applications |
iOS certificate pinning |
mobile application vulnerability assessment |
mobile application security assessment |
mobile app security analysis |
secure mobile application development practices |
android app security testing |
iOS app security testing |
android certificate pinning |
MobSF
Testing In Mobile Applications In today’s world, the significance of mobile applications in our ...
Continue Reading
The reason I stopped using Postman for API Pentests
I’ve been a proponent of Postman for a number of years. I’ve written and spoken about using it in ...
Continue Reading
Exploring Sentry Safe Exploit on the Flipper Zero with Logic Analyzer
hacking |
hardware |
flipper zero |
sentry |
safe |
logic analyzer
Overview I recently had a friend that wanted to learn how to use a logic analyzer. Given the number ...
Continue Reading
Webcast: Minor Flaws, Cumulative Risks
Imagine unraveling a classic whodunit murder mystery, where every subtle clue—a misplaced glove, a ...
Continue Reading
Mission Imfuzzable: How to Fuzz Web Apps you can't Intercept
Introduction Fuzzing is a critical technique for finding vulnerabilities in web applications by ...
Continue Reading
Webcast: Thrift Store Cracking Server: Popping Hashes Guide
(image was generated by Stable Diffusion, and is not an accurate representation of our cracking ...
Continue Reading
Taming the Enterprise AI Beast Webcast
As artificial intelligence (AI) continues to become more and more integral to business operations, ...
Continue Reading
12 Hacks of Christmas Day 12: Twelve Drummers Deleting Digital Clutter
🎵 On the twelfth day, clear digital clutter with twelve drummers deleting. Regularly review and ...
Continue Reading
12 Hacks of Christmas Day 11: Eleven Pipers Practicing Safe Browsing
🎵 On the eleventh day, practice safe browsing with eleven pipers practicing. Be mindful of the ...
Continue Reading
12 Hacks of Christmas Day 10: Ten Lords a-Cautious Shopping
🎵 On the tenth day, be cautious when shopping with ten lords a-cautious shopping. Stick to ...
Continue Reading
Nine Ladies Dancin' on Secured Networks
🎵 On the ninth day, keep your network secure with nine ladies dancin'. Protect your Wi-Fi network ...
Continue Reading
12 Hacks of Christmas Day 8: Eight Maids-a-Back-Up Singing
🎵 On the eighth day, safeguard your data with eight maids-a-back-up singing. Regularly backup your ...
Continue Reading
12 Hacks of Christmas Day 7: Seven Swans a-Encrypting
🎵 On the seventh day, protect your data with seven swans encrypting. Encrypt sensitive ...
Continue Reading
12 Hacks of Christmas Day 6: Six Geese-a-Layered Security
🎵 On the sixth day, adopt six geese-a-layered security. Implement a multi-layered security ...
Continue Reading
12 Hacks of Christmas Day 5: Five Golden Updates
🎵On the fifth day, gift yourself five golden updates. Ensure all your devices and software are up ...
Continue Reading
Day 4: Four Calling Bird's Eye View of Scams
🎵On the fourth day, keep an eye on scams with four calling birds. Be cautious of phishing emails ...
Continue Reading
Day 3: Three French Hens – Privacy for All Friends
🎵 On the third day, ensure privacy for all your friends with three French hens. Review your social ...
Continue Reading
12 Hacks of Christmas Day 2: Two-Turtle Authentication Unveiled
🎵 On the second day of Christmas, enhance your security strategy with two-turtle authentication. ...
Continue Reading
12 Hacks of Christmas Day 1: A Partridge in a Secure Password Tree
🎵 On the first day of Christmas, my true love gave to me: a partridge in a secure password tree. ...
Continue Reading
The 12 Hacks of Christmas: Cybersecurity Edition Series
The holiday season is here, bringing with it a whirlwind of festivities, joy, and, unfortunately, a ...
Continue Reading
Thanksgiving Hacks: Recipes for Cybersecurity Success
As we gather around the table to celebrate Thanksgiving, it's essential to extend our gratitude to ...
Continue Reading
What is Multi-Factor Authentication (MFA)?
Multi-factor authentication (MFA), also known as two-factor authentication (2FA) or two-step ...
Continue Reading
Encrypting Data on the Steam Deck with Plasma Vaults
encryption |
Gaming |
Privacy |
Steam Deck
In my previous post about the Steam Deck we discussed some of the privacy and security concerns ...
Continue Reading
Using PETaaS to Lower Your Cyber Insurance Costs
Modern networks have more than their fair share of risks, with the most damaging often being data ...
Continue Reading
The Do's and Don'ts for Building a Strong Password
Cyber Security Awareness Series
Continue Reading
Flipper Zero: A Hardware Hacking Multitool Webcast
Training |
hacking |
hardware |
webcast |
flipper zero
The Flipper Zero is known as a hacking multitool. It can cover a range of hacking from sub-ghz ...
Continue Reading
CyberScream - Hacking Like a Ghost(face)
consulting |
data breach |
penetration testing |
professionally evil |
hacking |
analysis |
cybersecurity |
pentesting |
phishing |
security breach |
exploits |
Halloween |
webcast
It’s that most hauntingly wonderful time of year again! Halloween is upon us, along with the dread ...
Continue Reading
Top Ten AWS Security Configurations: Mitigating Risk in the Cloud
In an era of increasing cloud adoption, businesses must prioritize implementation of robust ...
Continue Reading
Backups Won't Stop Ransomware
Ransomware attacks can have devastating consequences for organizations of all sizes and sectors, ...
Continue Reading
Navigating Cloud Security Webcast
In today's fast-paced digital landscape, organizations embrace the cloud as a cornerstone of their ...
Continue Reading
Bird's Eye View: Navigating the Landscape of Kubernetes Security
Ready to dig into the world of Kubernetes security like never before? Join Secure Ideas’ own Cory ...
Continue Reading
Navigating Evolving Regulations: Staying Ahead of Change
In today's rapidly expanding business world, the only constant seems to be change itself. One of ...
Continue Reading
Unleashing the Power of Flipper Zero: A Hacker's Multitool Webcast
Training |
wireless |
webcast |
flipper zero
In the ever-evolving world of technology, the Flipper Zero has emerged as a game-changer, making ...
Continue Reading
Sailing into the Unique Security Risks of AI Systems Part 1
As we venture further into the vast ocean of Artificial Intelligence (AI) - employing it to ...
Continue Reading
Finding Your Spidey Sense
Welcome, fellow web-slingers of the digital realm! Like our friendly neighborhood superhero, ...
Continue Reading
Beyond Hacking: Expanding Your Security Arsenal
Understanding the Need for Penetration Testing You’ve been told you need a penetration test. Maybe ...
Continue Reading
Quick Bites Episode 8 - (Back From the) Dead Space
hacking |
Quick Bites |
exploits |
MOVEit |
MOVEit Transfer |
SQL Injection |
Patching
For the last couple weeks, I’ve been replaying the original Dead Space trilogy - for those of you ...
Continue Reading
Understanding Server-Side Template Injection (SSTI)
Testing |
Training |
QA |
web penetration testing |
penetration testing |
application security |
OWASP |
web application security |
methodology |
OWASP Top 10
Web applications play a vital role in delivering dynamic content to users. To achieve this, ...
Continue Reading
Introducing SamuraiWTF 5.3: A Powerhouse for Web App Pen Testing
Testing |
Training |
samuraiWTF |
web penetration testing |
application security |
professionally evil |
Secure Ideas |
hacking |
OWASP |
Project
We are thrilled to announce the release of SamuraiWTF (Web Training Framework) version 5.3! This ...
Continue Reading
Introducing BILE - Groundbreaking Classification for Web App
Training |
penetration testing |
OWASP |
web application security |
BILE |
OWASP Top 10 |
BILE Classification Scheme |
vulnerability classification
As a seasoned web application penetration tester, I've always felt that there should be a more ...
Continue Reading
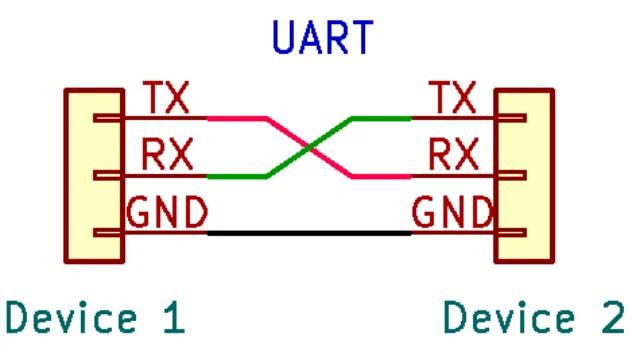
Hardware Hacking: Interfacing to UART with Your Computer
In my previous article, we covered identification and mapping of the UART interface. In that ...
Continue Reading
Hardware Hacking: Finding UART Pinouts on PCBs
In my previous article, we started to explore the Universal Asynchronous Receiver/Transmitter ...
Continue Reading
Hardware Hacking: Introduction to the UART Interface
I wanted to provide some information about hardware and firmware hacking in our blogs. To get the ...
Continue Reading
Introducing PETaaS®: Professionally Evil Testing as a Service
We're thrilled to announce the launch of our latest offering: Professionally Evil Testing as a ...
Continue Reading
Ace CISSP Exam Prep with ChatGPT: Your AI Study Buddy
Are you preparing for the CISSP exam or any other exam that requires a deep understanding of ...
Continue Reading
Why we ditched LastPass
LastPass is a very popular password management service with both personal and business solutions. ...
Continue Reading
Is the CISSP Mentorship for me?
“Knowledge is power.” That quote has been said more times than you can count because it’s true. The ...
Continue Reading
What happened to CVE-2022-23529? And what can we learn from it?
If you saw the disclosure notice for the flaw CVE-2022-23529, it would have been presented as a ...
Continue Reading
Risks of AI Generated Content, According to an AI Content Generator
AI and Machine Learning (ML) have become increasingly popular tools in various industries, ranging ...
Continue Reading
Quick Bites 7 - Dr. TamperMonkey (Or: How I Learned to Stop Worrying and Love JavaScript)
We get really excited here at Secure Ideas about sharing knowledge with others. Our mission ...
Continue Reading
Steam Deck Privacy and Security
Like any portable computing device, there are going to be questions about privacy and security. The ...
Continue Reading
ZAPmas Feedback
Testing |
open source |
web penetration testing |
OWASP |
mobile application |
web application security |
API
Sometimes Christmas comes early, and in this case for me it was the publication of the Twelve Days ...
Continue Reading
12 Days of ZAPmas - Day 12 Testing a new Content-Security-Policy
What is the CSP? The Content-Security-Policy (CSP) is a widely recommended control and is ...
Continue Reading
Twelve Days of ZAPmas - Day 11 - ZAP impressions from a Burp user
It probably seems a bit odd to do this on Day 11 and not at the end of the series, but I have one ...
Continue Reading
Twelve Days of ZAPmas - Day 10 - Manual Web App Testing Unproxied
Most of the time, proxying the browser doesn’t present any sort of trouble. You should be able to ...
Continue Reading
Twelve Days of ZAPmas - Day 9 - Automated Scanning and ATTACK mode
Automated scanning against an application is useful. It’s a faster and less labor-intensive way to ...
Continue Reading
Twelve Days of ZAPmas - Day 8 - Spidering
Spidering is an automated process that recursively finds and follows all the navigation from an ...
Continue Reading
Twelve Days of ZAPmas - Day 7 - API Testing with Postman and ZAP
If you’ve done any significant amount of API development, there’s a good chance you’ve used ...
Continue Reading
Twelve Days of ZAPMAS - Day 6 - Passive Flaw Detection and Using the HUD
One of the awesome things about a security-focused interception proxy like ZAP is its ability to ...
Continue Reading
Twelve Days of ZAPmas - Day 5 - Scope and Contexts
Normally I don’t like having my interception proxy hide out-of-scope traffic. Doing so creates a ...
Continue Reading
Twelve Days of ZAPmas - Day 4 - Fuzzing for Injection
I briefly introduced fuzzing earlier in the series, citing it as the second primitive upon which ...
Continue Reading
Twelve Days of ZAPmas - Day 3 - CYA (Cover Your Auth)
Access control is one of the crucial elements to application security. The vast majority of ...
Continue Reading
Twelve Days of ZAPmas - Day 2 - The Edge of Tomorrow
Day 2 - The Edge of Tomorrow - Replaying and Tampering with Requests Fuzzing and tampering are like ...
Continue Reading
Twelve Days of ZAPmas - Day 1 - Setting Up ZAP
This holiday season, I’m going to run down some of the ins and outs of working with OWASP Zed ...
Continue Reading
Quick Bites Ep 6 - Good Hygiene is IMPORTANT, PEOPLE!
Guidance |
best practices |
Quick Bites |
Cyber |
Hygiene |
CIS Top 18 |
Blue Team
So, I just missed a week of work because of the flu (it wasn’t COVID, I got tested). The flu SUCKS. ...
Continue Reading
How to iterate through advfirewall rules
Training |
professionally evil |
Secure Ideas |
Windows 10 |
Windows 11 |
sysadmin |
system administration |
cmd |
powershell |
firewall rules
There are several ways to pull firewall information from a Windows system. Today we will leverage ...
Continue Reading
Introduction to Writing Nmap Scripting Engine (NSE) Scripts
NMAP |
programming |
NSE
One thing I notice a lot of people are missing in their skill set as security professionals is the ...
Continue Reading
Quick Bites Ep 5 - The Call Is Coming From INSIDE THE HOUSE
hacking |
Quick Bites |
Insider Threat |
Attacks |
Halloween
Man, I’ll be honest - I’m super excited to be doing a Halloween-themed blog post this year. So, ...
Continue Reading
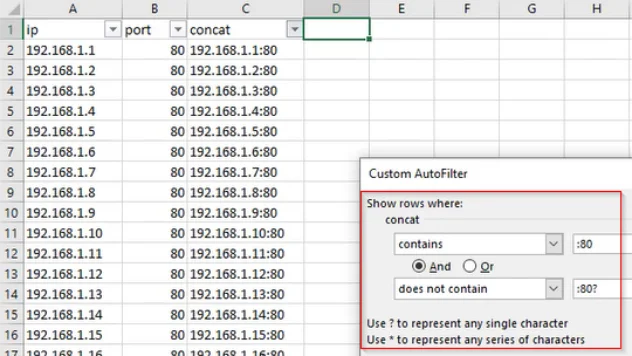
Working With Data: IP and Port Filtering
Training |
professionally evil |
Secure Ideas |
technology tips and tricks |
sysadmin |
data |
data manipulation |
excel |
spreadsheet |
filtering
During our day-to-day work, there’s a lot of data that we interact with. In order to make good use ...
Continue Reading
Coming Soon - Twelve Days of ZAPmas
In December of 2018, I published a twelve-day series of cross-site scripting tips, tricks, and ...
Continue Reading
Nmap vs. Masscan
hacking |
NMAP |
port scanning |
masscan |
host discovery
If you are in IT, chances are you have at least heard of Nmap and Masscan. Both are free and ...
Continue Reading
Quick Bites Ep 4 - Let's Talk About SSRF, Baby!
Let’s talk about you and (application) secur-i-ty! Let’s talk about all the good things and the bad ...
Continue Reading
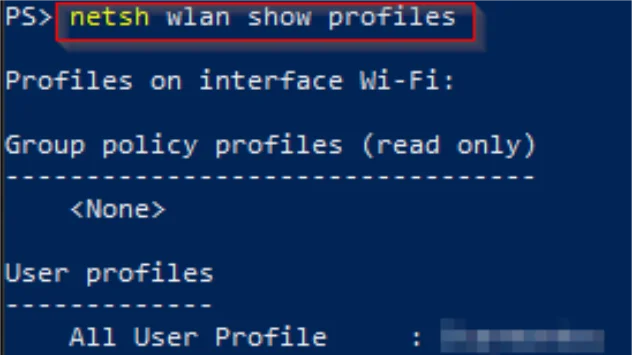
View Wireless Profile Password Information Using PowerShell or CMD
Training |
professionally evil |
Secure Ideas |
hacking |
Windows |
Windows 10 |
Windows 11 |
sysadmin |
system administration |
cmd |
wireless |
wifi |
wifi password |
powershell |
wireless profile
There are a couple different ways for you to access your Windows wireless password information. If ...
Continue Reading
What are the key requirements of the GLBA Safeguards Rule?
information security |
penetration testing |
CISSP |
education |
compliance |
risk assessment |
security controls |
information security program |
GLBA |
Safeguards Rule |
Dec 9, 2022 |
automotive |
banking |
vulnerability assessment
The Gramm-Leach-Bliley Act (GLBA) contains the Safeguards Rule. This requires financial businesses ...
Continue Reading
JuiceShop Workshop in less than 5 minutes
Training |
application security |
OWASP |
AWS |
IaC |
JuiceShop |
Containers |
AWS_ECS |
workshops |
Vagrant |
AWS-CDK
Have you ever deployed 10-30 containers in AWS with the single stroke of a key? (well if you don’t ...
Continue Reading
How to Obfuscate Strings in Rust the Easy Way Using the litcrypt Crate
Overview Static strings in a binary can make the life easier for reverse engineers, be those ...
Continue Reading
Application Security 202: Vulnerabilities Accepted
Testing |
Vulnerability |
Guidance |
data breach |
information security |
penetration testing |
application security |
professionally evil |
Secure Ideas |
hacking |
best practices |
cybersecurity |
Privilege Escalation
vul·ner·a·bil·i·ty The quality or state of being exposed to the possibility of being attacked or ...
Continue Reading
(Not So) Quick Bites - Episode 3 - Writing About Writer's Block
Deliverables |
consulting |
application security |
Secure Ideas |
cybersecurity |
methodology |
Project |
Writing |
Quick Bites
So, sometimes I have a real problem with writing, specifically reports and blog posts. Somehow, ...
Continue Reading
How to allow multiple RDP sessions
Training |
penetration testing |
pentesting |
Windows |
technology tips and tricks |
rdp |
sysadmin |
system administration
The goal of this article is to walk through how to set up a Windows host to allow multiple remote ...
Continue Reading
Hunting Secrets
Applications are hemorrhaging sensitive data. In many cases, the culprit is marketing and analytics ...
Continue Reading
Ensuring Web Security via Ansible (Apache)
NOTE: even though this will require Ansible, you can run this on any operating system contrary to ...
Continue Reading
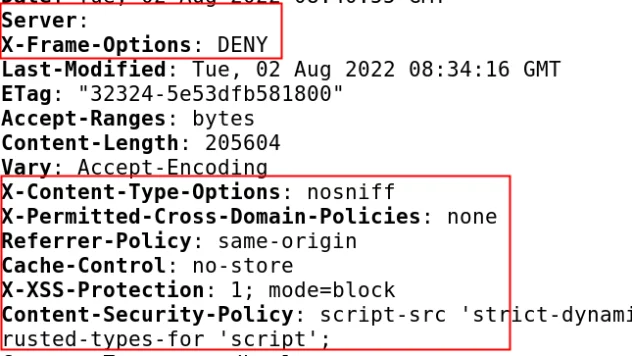
Why your application needs a Content Security Policy (And How to Build One)
As a web application owner, it is crucial to understand the concept of a content security policy ...
Continue Reading
Quick Bites Episode 2 - HTTP Security Headers and Why You NEED Them
Hi everybody! So, after some feedback about the last “quick” Quick Bites (thanks Josh!), I’ve ...
Continue Reading
Privilege Escalation via File Descriptors in Privileged Binaries
application security |
professionally evil |
Secure Ideas |
Linux |
programming |
File Descriptors |
SetUID |
Privilege Escalation
Today I wanted to cover an application security topic that applies to SetUID binaries. As we all ...
Continue Reading
How to Update the Nmap OUI Database
network |
professionally evil |
Secure Ideas |
NMAP |
Linux |
IEEE |
OUI |
nmap-mac-prefixes
Overview In a previous blog post, I covered what an OUI is, how to extract them from a MAC address, ...
Continue Reading
Of MAC Addresses and OUI: A Subtle, but Useful, Recon Resource
network |
professionally evil |
Secure Ideas |
MAC Address |
IEEE |
OUI |
PENT
When it comes to reconnaissance, every little bit of information can be helpful. Today, we will ...
Continue Reading
The Other Replicating Directory Changes
Quick Summary The Replicating Directory Changes right in Active Directory allows you to request ...
Continue Reading
Quick Bites - Finding Open Windows File Shares
Vulnerability |
network |
Secure Ideas |
hacking |
network security |
Windows |
scanning |
methodology |
how-to |
Free
Hi there, ladies and gentlemen! My name is Aaron Moss, and welcome to the first edition of Quick ...
Continue Reading
LD_PRELOAD: Making a Backdoor by Hijacking accept()
application security |
professionally evil |
Secure Ideas |
LD_PRELOAD |
accept |
dup2 |
make |
Linux |
programming |
Shared Objects |
dlsym |
shell |
backdoor |
rootkit |
userland |
ELF |
inject |
injection
Today I want to continue the series on using LD_PRELOAD. In previous posts, we covered how to ...
Continue Reading
PowerShell Tips: How do I Mount a VHD or Lock a BitLocker Drive?
encryption |
security |
professionally evil |
Secure Ideas |
getting started |
BitLocker |
VHD |
rtfm |
manage-bde |
mount-vhd |
manage bitlocker |
technology |
technology tips and tricks |
Windows 10 |
VHDX |
encrypted drive |
technology tips |
how-to |
btfm |
Windows 11
PowerShell Tips How do I Mount a VHD or Lock a BitLocker Encrypted Drive?
Continue Reading
How to Create Custom Probes For NMAP Service/Version Detection
network |
hacking |
cybersecurity |
pentesting |
scanning |
NMAP |
version |
service |
probe |
ports |
match |
chrome |
debugging |
nmap-service-probes |
softmatch |
rarity |
directive |
remote
Overview NMAP is a fantastic tool for performing initial reconnaissance and enumeration. A simple ...
Continue Reading
How to verify PGP signatures
how to verify pgp signature |
how to use pgp signature |
pgp signature check |
how to verify gpg signatures |
pgp digital signatures |
gpg signatures |
verify gpg signatures
PGP (Pretty Good Privacy) is an encryption software that is mostly known for its use in email. It ...
Continue Reading
Digging Between the Couch Cushions - CouchDB CVE-2021-38295 Breakdown
Vulnerability |
developers |
security |
open source |
information security |
application security |
hacking
Introduction In this blog post we’re going to take a look at the recent CouchDB vulnerability, ...
Continue Reading
Linux X86 Assembly - How To Test Custom Shellcode Using a C Payload Tester
Overview In the last blog post in this series, we created a tool to make it easy to build our ...
Continue Reading
Low Hanging Fruit Ninja: Slashing the Risks of the Human Element
A long time ago in a galaxy far, far away, I was not a Security Consultant. I was a Chef. And I ...
Continue Reading
How to configure BurpelFish
I recently was doing a pentest and was continuously looking up translations for words, and thought ...
Continue Reading
Linux X86 Assembly - How To Make Payload Extraction Easier
Overview In the last blog post of the X86 Linux assembly series, we focused on how to make our ...
Continue Reading
Linux X86 Assembly - How to Make Our Hello World Usable as an Exploit Payload
Overview In the last two tutorials, we built a Hello World program in NASM and GAS for x86 ...
Continue Reading
Run as Admin: Executive Order on Cybersecurity
On May 12, 2021, President Biden issued an executive order on cybersecurity. This new order ...
Continue Reading
Linux X86 Assembly - How to Build a Hello World Program in GAS
Overview In the last tutorial, we covered how to build a 32-bit x86 Hello World program in NASM. ...
Continue Reading
Linux X86 Assembly - How to Build a Hello World Program in NASM
Overview A processor understands bytecode instructions specific to that architecture. We as humans ...
Continue Reading
AppSec Cheat Code: Shift Left, Shift Right, Up, Down & Start
Seamless and unobtrusive security is the future. We are huge advocates of shifting left and moving ...
Continue Reading
A Hacker’s Tour of the X86 CPU Architecture
Overview The Intel x86 CPU architecture is one of the most prolific CPU architectures for desktops, ...
Continue Reading
Three Excellent API Security Practices Most People Neglect
We are very much in the age of APIs. From widely-used single-purpose products like Slack to ...
Continue Reading
LD_PRELOAD: How to Run Code at Load Time
Today I want to continue the series on using LD_PRELOAD. In previous posts, we covered how to ...
Continue Reading
Announcing Burp Co2!
This is for those of you who do web pen testing with Portswigger’s Burp proxy tool! Over the past ...
Continue Reading
Converting NMAP XML Files to HTML with xsltproc
NMAP is a wonderful network scanner and its ability to log scan data to files, specifically XML, ...
Continue Reading
3 Reasons to Pentest with Brave
3 Reasons to Pentest with Brave November 30, 2020 March 19, 2021 / By Ochaun Marshall Penetration ...
Continue Reading
Not-So-Random: Using LD_PRELOAD to Hijack the rand() Function
Today I wanted to continue the series on using LD_PRELOAD. In today’s post we are going to use ...
Continue Reading
Boolean Math (NOT Logic) – CISSP Domain 3
Hello everyone. We’ve got another Boolean math session lined up for you today. This time we’re ...
Continue Reading
The Death and Rebirth of Musashi.js OR How I turned personal failure into better teaching tools.
A little background… As I stood in front of a class of developers trying to explain cross-origin ...
Continue Reading
Boolean Math (XOR Logic) – CISSP Domain 3
Hello everyone. We’ve got another Boolean math session to look over today. Our focus this time will ...
Continue Reading
LD_PRELOAD - Introduction
Today I wanted to start what I plan to be a small series of blog posts about LD_PRELOAD. LD_PRELOAD ...
Continue Reading
Boolean Math (OR Logic) – CISSP Domain 3
Today we are going to take another look at some Boolean mathematics. In particular, we’re going to ...
Continue Reading
Proxies, Pivots, and Tunnels - Oh My!
Forward When talking about a proxy or a pivot or a tunnel, we could be talking about very different ...
Continue Reading
Boolean Math (AND Logic) - CISSP Domain 3
Today we’re going to take a quick look at the AND Boolean logic, which is covered in Domain 3 of ...
Continue Reading
How to configure Android (Virtual) for Mobile PenTest
Setting up your environment for a mobile application penetration test can be a chore, especially if ...
Continue Reading
Game Hacking Part 1 - Equipping Your Loadout
Why Bother with Video Game Security? Video games are more than just entertainment. Gaming is a ...
Continue Reading
The OPSEC of Protesting
For the past three months thousands of people have been protesting in the United States due to the ...
Continue Reading
Encryption – CISSP Domain 3
We’re circling back to some more CISSP-related materials. Today’s topic will be encryption, which ...
Continue Reading
Encoding – CISSP Domain 3
Today we’re going to take a quick look at encoding, as covered in Domain 3 of the CISSP common body ...
Continue Reading
Summer Internship at Secure Ideas
This past summer, I worked as an intern for Secure Ideas. My role at the company was that of ...
Continue Reading
Bash Tips and Tricks
I know I definitely identify with being a visual learner, and I am happy to help where I can with ...
Continue Reading
Hashing Functions – CISSP Domain 3
Today we’re going to take a quick look at hashing functions, as covered in Domain 3 of the CISSP ...
Continue Reading
Visual Learner? Look no further!
Secure Ideas has been in the business for 10 years and over the last ten years we have found that ...
Continue Reading
Waving the White Flag: Why InfoSec should stop caring about HTTPOnly
As a company that is constantly working with our penetration testing clients on understanding where ...
Continue Reading
Has contents: true
Total pages: 2
Current page: 0








-1.png)

.png)
.jpg)


.png)





























%2c%20How%20to%20Identify%20Them%2c%20and%20How%20to%20Prevent.png)


.png)














.png)

.png)

.png)
.png)
.png)











.png)






-1.webp)