NMAP is a wonderful network scanner and its ability to log scan data to files, specifically XML, helps quite a bit. This enables the scan data to be parsed by other tools such as Metasploit’s db_import or even NMAP’s own Zenmap GUI. While XML is great for parsing, it’s not really easy for humans to read. I have found several people are unaware of the fact that the NMAP XML file can also be converted into a nicely formatted HTML file via the use of a tool called xsltproc. Today I want to give a quick rundown of how to do that from start to finish using a Kali Linux VM and Metasploitable2 VM.
Lab Setup
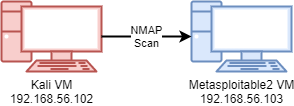
The setup for this exercise used two lab VMs. One was a Kali VM, the other was a Metasploitable2 VM. The Metasploitable2 VM serves as a target to be scanned via NMAP from the Kali VM. The diagram below shows the configuration of the lab.
Scanning to Create the XML Scan Data File
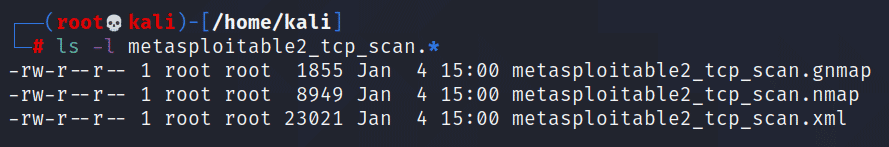
From the Kali VM we want to scan all TCP ports on the Metasploitable2 VM and also run it with version detection and default scripts. I generally like to log in all data formats using the -oA [filename_prefix] switch and argument. If you are looking to only get the XML file then you could use the -oX switch instead. For this lab, I used the following command as root to run the scan:
| nmap -sTV -p- -A -vvvv -oA metasploitable2_tcp_scan 192.168.56.103 |
A breakdown of the switches in that command are as follows:
| Command Part | Description |
| nmap | The NMAP command inself. |
| -sTV | TCP connect scan with version detection |
| -p- | Port selection: All ports from 1-65535 |
| -A | Enables several modes. This enables version & OS detection, runs default scripts, and runs a traceroute against the system. |
| -vvvv | Very high level of verbosity |
| -oA metasploitable2_tcp_scan | Output data in “All” formats, this will result in a NMAP text file, grepable file, and XML file. The string that follows the switch is the filename prefix. |
| 192.168.56.103 | The target host being scanned. This is the IP address of the Metasploitable2 VM. |
Once it was finished we can see the three file it created from the -oA switch:
Converting the XML File into an HTML File
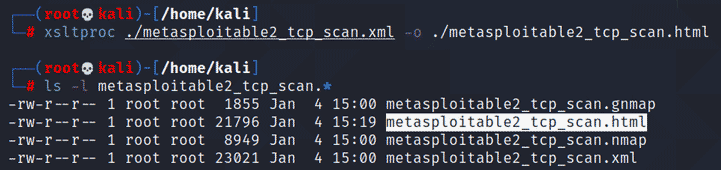
This is where the xsltproc comes in. This tool can be used to convert the XML file into a nicely formatted HTML file. To perform this conversion, run the following command:
| xsltproc metasploitable2_tcp_scan.xml -o metasploitable2_tcp_scan.html |
This command will run and if successful, it will just silently exit. However it will generate a new file called metasploitable2_tcp_scan.html as shown below.
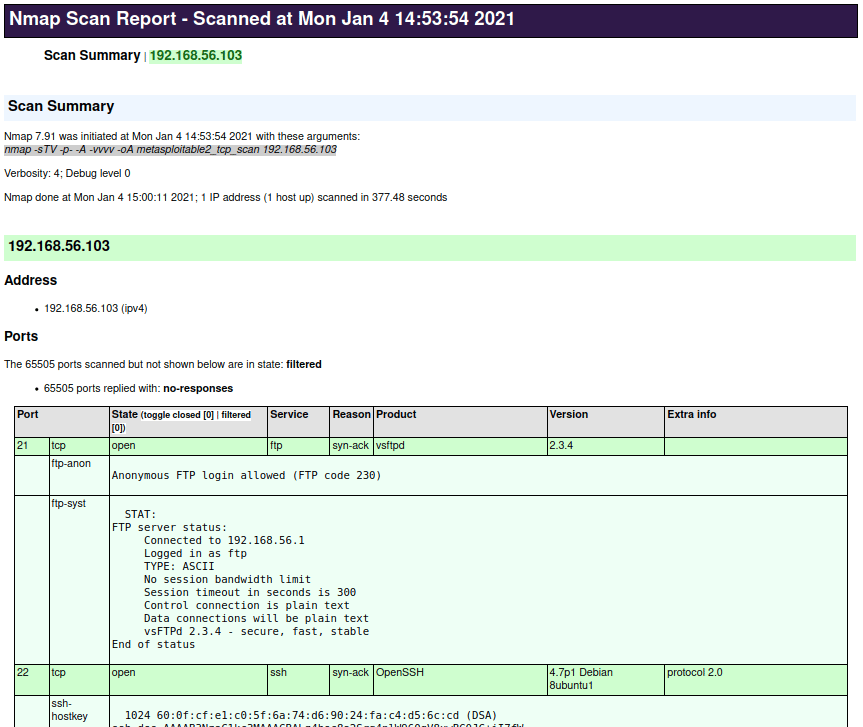
Viewing the Results
Now that we have the HTML file, it can be viewed in the web browser of your choice. The HTML file is designed to be a nice, clean, table-based report. Any scripts that produced output during the scan will be in the rows underneath the corresponding port and it will use a lighter color shade as the background color of the report. The screenshot below shows a sample of what this file looks like:
Conclusion
I hope you’ve enjoyed this blog post and learned something new today about NMAP XML files. If you’re interested in security fundamentals, we have a Professionally Evil Fundamentals (PEF) channel that covers a variety of technology topics. We also answer general basic questions in our Knowledge Center. Finally, if you’re looking for a penetration test, professional training for your organization, or just have general security questions please Contact Us.
