Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Exploring Sentry Safe Exploit on the Flipper Zero with Logic Analyzer
Overview I recently had a friend that wanted to learn how to use a logic analyzer. Given the number of applications available for the Flipper Zero, I anticipated there might be some promising targets worth studying. One that I found was the Sentry safe exploit FAP by Etienne Sellan, aka Hackd4ddy, ...
Continue Reading
Never miss a Professionally Evil update!
Webcast: Thrift Store Cracking Server: Popping Hashes Guide
(image was generated by Stable Diffusion, and is not an accurate representation of our cracking ...
Continue Reading
Flipper Zero: A Hardware Hacking Multitool Webcast
Training |
hacking |
hardware |
webcast |
flipper zero
The Flipper Zero is known as a hacking multitool. It can cover a range of hacking from sub-ghz ...
Continue Reading
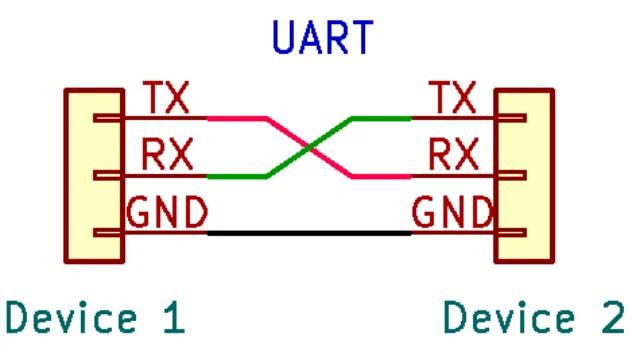
Hardware Hacking: Interfacing to UART with Your Computer
In my previous article, we covered identification and mapping of the UART interface. In that ...
Continue Reading
Hardware Hacking: Finding UART Pinouts on PCBs
In my previous article, we started to explore the Universal Asynchronous Receiver/Transmitter ...
Continue Reading
Hardware Hacking: Introduction to the UART Interface
I wanted to provide some information about hardware and firmware hacking in our blogs. To get the ...
Continue Reading
Has contents: true
Total pages: 1
Current page: 1