If you are in IT, chances are you have at least heard of Nmap and Masscan. Both are free and open-source tools that can be used for similar purposes, but both have areas where they really shine. Let’s break them down and then discuss where we would use one, or both to get our desired results.
Nmap is short for “Network Mapper” and was originally released in September 1997 by Gordon Lyon. It has been through ten or so releases and has really matured and developed into a tool that everyone turns to when they need to scan a network for devices, services, open ports or troubleshoot network issues. It’s most commonly used as a Linux command line tool, but most operating systems are supported. If you are looking for a GUI version, check out Zenmap. Although the command line version really is the way to go in my opinion. Zenmap works perfectly fine but those that have become accustomed to some of the slick graphics and flashy user experiences may find it a little dated.
Masscan is something that early in my career I heard used interchangeably with Nmap. As if you could choose one or the other based on personal preference. I soon found out this was not at all the case. Masscan was, according to its creator Robert Graham, created to scan the entire internet as fast as possible. What? The entire internet. Yes, you heard me. That still must take forever you say? If you are waiting outside the bathroom door, then maybe six minutes can seem like forever, yes. In this case, it’s incredibly fast. Let that sink in for a minute. Six minutes. The entire internet.
Masscan utilizes an asynchronous transmission architecture to send out probes without waiting for replies. Because of this, you have the ability to transmit up to ten million packets per second. How fast you can actually scan is going to depend on a few factors, like your system’s resources, bandwidth, and which OS you are using. Masscan is available for Linux, Mac, Windows or FreeBSD, but Linux will be the fastest.
So when do we use one or the other? In many cases, I might use Masscan in tandem with Nmap. The Masscan author has made every effort to make it familiar and compatible with Nmap settings, so jumping right in if you are already familiar with Nmap isn’t too much of a leap. Here’s a typical scenario. We are performing an internal network test for a client. They have provided us with their internal IP’s. Here they are:
- 10.246.0.0/16
- 10.100.31.0/21
- 10.253.253.0/24
- 10.240.240.0/24
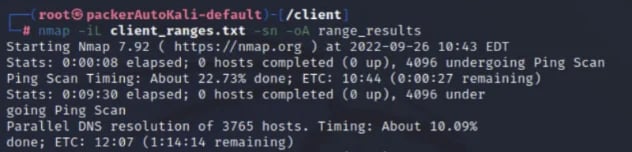
Let’s throw these in Nmap on our Kali VM and see what we have going on. Right now I just want to see what hosts are live on this network. I’m going to create a file called client_ranges.txt and run this pretty simple command:
nmap -iL client_ranges.txt -sn -oA range_results
This is telling Nmap to scan the ranges in this file (-iL client_ranges.txt), only doing host discovery (-sn)and to output the results to all three formats(-oA range_results), which will be an XML file (range_results.xml), a normal text file (range_results.nmap), and a greppable file (range_results.gnmap), into a file named range_results. When I run this scan with Nmap, my Kali is telling me this is going to take at least an hour and 15 minutes as we can see below. And this is just an estimate based on its current mood. I’ve seen scans this size go all day.
If you are familiar with subnets and CIDR network references you might recognize that the /16 subnet we've been given can contain over 65,000 possible IP addresses. So we are scanning tens of thousands of IP’s with just these four ranges. I don’t want to wait that long. I have a network to hack. Masscan to the rescue! Since Masscan can do this much quicker, here is the command I am going to feed it:
masscan -iL client_ranges.txt -p22,25,80,389,443,445,3389,8000,8080,8443 -oG masscan.grep --rate 3000
Masscan is able to use the -iL functionality from Nmap to scan our client_ranges.txt file, but whereas Nmap will by default scan the most common 1,000 ports, we have to tell Masscan what ports we want it to scan. Since this is an internal test, I am going to focus on the ten ports listed after the -p. -oG will give me a grepable file to parse through, and –rate 3000 is going to dictate the speed for this internal network. Masscan is incredibly fast and can burn down a network if you don't tell it not to. You can see the massive reduction in timing using Masscan below.
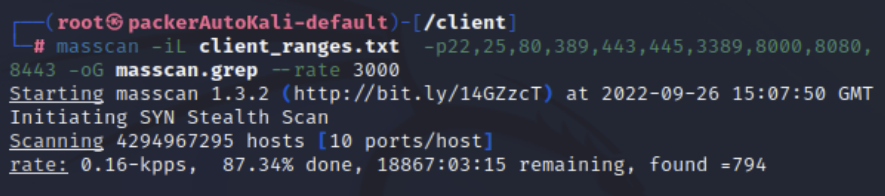
It finished in less than four minutes total. Once Masscan is finished, we can run the following command to extract a list of unique live hosts from the results and place them into a new file:
awk '/Host/ {print $4}' masscan.grep | sort -uV > live-hosts.masscan
So, now we know what’s sitting on this network and can move on to our next step in evaluating and identifying security vulnerabilities. I might utilize Nmap again by running one of the numerous Nmap Scripting Engine (NSE) scripts that are available such as smb-enum-users.nse to enumerate all users available on a Windows system. Or to log into the MySQL server if it’s been left as root or anonymous, with mysql-empty-password.nse
Keep in mind this is a very basic use case for Nmap and Masscan. Both have more they can do, and Nmap in particular is much more granular. You can think of Masscan as a scout - it runs out there and quickly comes back and tells you what it saw. Then Nmap would be a cartographer - it goes out and comes back with a detailed map and far more information, but it takes longer as a result. To get more familiar with Nmap, check out these great blog posts from Secure Ideas Senior Security Consultant Travis Phillips Converting NMAP XML Files to HTML with xsltproc and How to Create Custom Probes For NMAP Service/Version Detection
Nmap still really is the undisputed King of Network Port Scanners. But when you feel the need, the need for speed, Masscan does a fine job of being top gun.