Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Rolling for Resilience Part 2: The Communication Gauntlet
This is the second post in this series addressing my perspective on the current state of ...
Continue Reading
Bypassing Browser PDF Security: Using Embedded JavaScript Forms for Social Engineering
I can say that, since I started my journey at Secure Ideas, I’ve felt extremely fortunate. Not only ...
Continue Reading
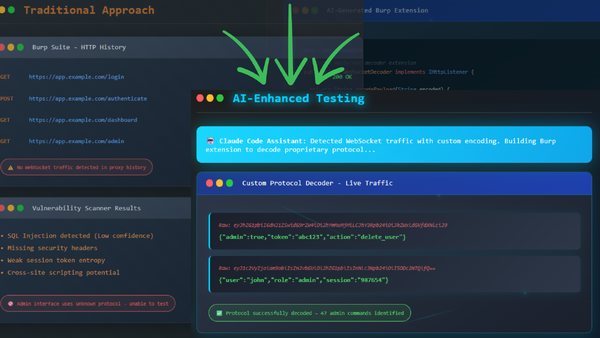
The Real AI Revolution in Penetration Testing
Custom Tooling at Lightning Speed Most cybersecurity professionals hear "AI in penetration testing" ...
Continue Reading
Quick Bites 13 – Network Pentest Restrictions Can Hurt Your Business
Too Many Network Pentest Restrictions Can Hurt Your Business
Continue Reading
But AI Can Give Me the Commands! Why You Still Need to Learn the Linux File System
Linux |
AI |
AI Security
It’s now easier than ever for AI to write your bash scripts or give you the exact command to ...
Continue Reading
Secure Password Management in PowerShell: Best Practices
When working with PowerShell to automate tasks, managing credentials securely is a critical ...
Continue Reading
Rolling for Resilience: A Strategic Guide to Cybersecurity Table-top Exercises
This is the first post in this series addressing my perspective on the current state of ...
Continue Reading
Risk-Driven Approach: The Federal Government’s Shift in Cybersecurity Burden
From All-Hazards to Risk-Informed The New Risk-Informed Paradigm One of the most significant shifts ...
Continue Reading
Understanding Garbage Findings
There is a well-meaning desire among penetration testers to produce findings. The fact of the ...
Continue Reading
Houston, We Have a Problem
Satellite Security Testing: A Holistic Approach Last month, I had the opportunity to present at ...
Continue Reading
Cybersecurity Essentials for SMBs: Building a Robust Program
When discussions arise around companies' cybersecurity programs, the focus often gravitates towards ...
Continue Reading
Has contents: true
Total pages: 32
Current page: 2

-1.png)

.png)
.jpg)


.png)