When it comes to reconnaissance, every little bit of information can be helpful. Today, we will look at MAC addresses, specifically the first 3 bytes, which serve as the Organizationally Unique Identifier, or OUI for short. The OUI can help get a picture of the devices on the network by using the publicly available IEEE registration information related to it. Today, we will explore how to look up IEEE OUI information, demonstrate examples of using this information, and some pitfalls to watch out for.
What is a MAC Address?
A MAC address is a Media Access Control address. These will consist of 48 bits (6 bytes) of data. For readability to humans, these will usually display in a series of hexadecimal octets separated by colons like the following:
DE:AD:BE:EF:CA:FE
In general and oversimplifying terms, this can be thought of as a unique address to identify a physical network interface, such as a wired Ethernet, Wi-Fi, or Bluetooth network card. We use the MAC for routing in the Ethernet layer (Layer 2) and it is used to directly address the hardware. For example, the screenshot below shows a Wireshark capture; you can see an IPv4 source and destination addresses at the lower parts of the packet. At the top, you have the Ethernet layer, which contains a source and destination MAC addresses.
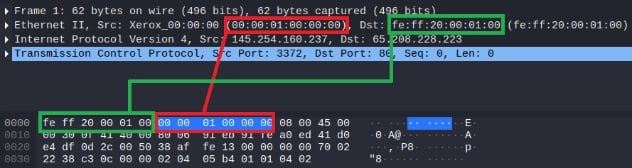
The vital thing to note here is that the MAC addresses come first, and the destination is the first 6 bytes of the packet. This allows simple layer 2 devices to only need the first 6 bytes to forward it. MAC addresses are also essential for other network protocols such as DHCP (Dynamic Host Configuration Protocol) and ARP (Address Resolution Protocol).
What is an OUI?
An OUI is a unique identifier that identifies an organization. The IEEE assigns these unique identifiers to companies that need to include them in a product with networking capability. The IEEE makes this information available to the public, and it is possible to determine what organizations own which OUI. This is interesting because this is included in a MAC address.
The OUI of a MAC Address
The MAC address consists of 6 octets. The first 3 octets of the MAC address are the OUI. So, for example, If we had a random MAC Address of A0:91:A2:01:02:03, the OUI would be A0:91:A2. The remaining 3 octets are effectively a serial number (often referred to as an extension identifier), and it’s up to the manufacturer how this part is determined. The image below shows this split out with callouts.
With the extension identifier, they could assign up to 16,777,216 devices with that OUI before it’s depleted. If they deplete the range, they would have to request another OUI. Manufacturers can have more than one OUI assigned to them, as is the case with companies like Apple or Xerox.
How-to: Look UP OUI Assignments
As mentioned earlier, the IEEE makes this information publicly available online. This information is available in a formatted plaintext format and is found at https://standards-oui.ieee.org/. The screenshot below shows what the formatting of this OUI file looks like.
It’s worth it to save this file locally from time to time since it is large, and this would offload bandwidth to the server. On the left side of this document, we see the OUI fields listed in two formats, XX-XX-XX and XXXXXX. If we follow our example earlier with the OUI of A0:91:A2, we could format it as A0-91-A2 or A091A2. Personally, I’m usually in favor of the XXXXXX format, but with the example OUI formatted as A091A2, we can use Ctrl+F to search for it. Doing so reveals that the MAC address's OUI belongs to OnePlus, as shown in the screenshot below.
Why is this interesting? Well, we can now know that OnePlus, a cell phone manufacturer, likely manufactured the device. If the OUI can be believed, we can assume that this device is a OnePlus cell phone. This is interesting on a LAN network, but can get even more interesting in the Wi-Fi arena.
Tools like Aircrack-ng’s airodump-ng lets you passively observe MAC addresses of Wi-Fi access points and their clients. Using that, you could get an idea on what sort of devices are connected to a given Wi-Fi network, or even client’s not connected but just happen to be nearby. For example, let's look at the example output from the airodump-ng’s documentation page.
CH 9 ][ Elapsed: 1 min ][ 2007-04-26 17:41 ][ WPA handshake: 00:14:6C:7E:40:80 |
Let’s try to determine the manufacture of these wireless devices using the OUI:
- APs:
- 00:09:5B => NETGEAR
- 00:14:6C => NETGEAR
- Clients:
- 00:0F:B5 => NETGEAR
- 00:14:A4 => Hon Hai Precision Ind. Co.,Ltd.
- 00:0C:41 => Cisco-Linksys, LLC
- 00:0F:B5 => NETGEAR
While this example covered how to manually lookup an OUI, it is worth noting that some tools, such as Wireshark and Nmap, will attempt to do this auto-magically for you, but using a local database file rather than online queries. It’s worth knowing how to do it yourself in case that DB file is out-of-date.
OUI Looks are Awesome - But Not Perfect
So this looks awesome! We can learn quite a bit from peeking at the OUI of devices. But you have to take it with a grain of salt. The OUI (and MAC address for that matter) can’t always be trusted, and here are a few reasons why. First, MAC addresses are easy to spoof. If you are on a Linux-based system, you can use tools like macchanger to change your MAC address. At this point, this OUI would be completely false. Android even has an option for this in the Developer Settings, as shown below.
There is also the possibility of not seeing the real source MAC address in a packet if it’s been through routing on the network. The source MAC address you’d see at this point is likely to belong to a switch or router that’s in the route between you and the other endpoint. Furthermore, some MAC addresses that contain OUI’s aren’t officially registered with the IEEE or are incorrect. Example, VirtualBox often uses 08:00:27. According to the IEEE, this belongs to PCS Systemtechnik GmbH. However, tools like Nmap will correctly identify it as Oracle VirtualBox Virtual NIC. Some vendors might be selling a cheap device and never paid to register for an OUI. The world isn’t perfect.
Conclusion
I hope you’ve enjoyed this blog post and learned something new about MAC addresses, OUIs, and the IEEE standards. If you’re interested in network security fundamentals, we have a Network Security channel that covers a variety of network topics. We also offer training via our Professionally Evil Network Testing (PENT) course. We also answer general basic questions in our Knowledge Center. Finally, if you’re looking for a penetration test, professional training for your organization, or just have general security questions, please Contact Us.