Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Evaluating AI Language Tutors Through a Security Lens
Evaluating AI Language Tutors Through a Security Lens Over the past year or so, I have seen a noticeable increase in AI-driven language learning tools. They are advertised as convenient, always-available tutors that can help you practice conversation in a low-pressure setting. As someone with a ...
Continue Reading
Never miss a Professionally Evil update!
Mobile Testing Considerations
penetration testing |
Secure Ideas |
cyber security |
mobile application security testing |
mobile app penetration testing |
mobile application development |
mobile application testing |
testing mobile applications |
iOS certificate pinning |
mobile application vulnerability assessment |
mobile application security assessment |
mobile app security analysis |
secure mobile application development practices |
android app security testing |
iOS app security testing |
android certificate pinning |
MobSF
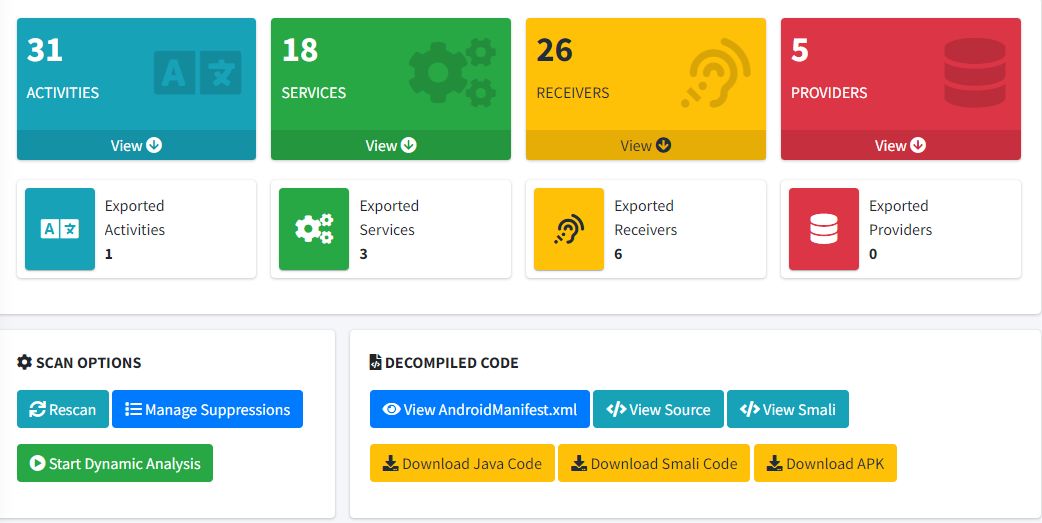
Testing In Mobile Applications In today’s world, the significance of mobile applications in our ...
Continue Reading
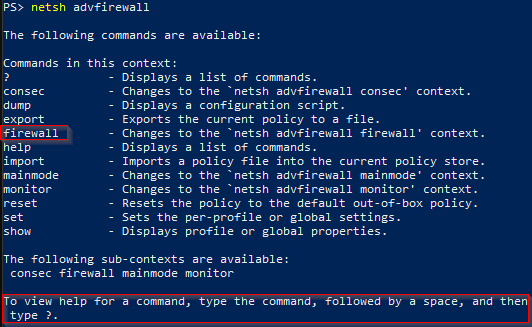
How to iterate through advfirewall rules
Training |
professionally evil |
Secure Ideas |
Windows 10 |
Windows 11 |
sysadmin |
system administration |
cmd |
powershell |
firewall rules
There are several ways to pull firewall information from a Windows system. Today we will leverage ...
Continue Reading
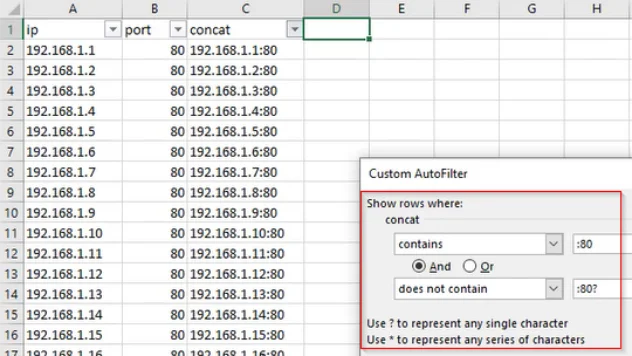
Working With Data: IP and Port Filtering
Training |
professionally evil |
Secure Ideas |
technology tips and tricks |
sysadmin |
data |
data manipulation |
excel |
spreadsheet |
filtering
During our day-to-day work, there’s a lot of data that we interact with. In order to make good use ...
Continue Reading
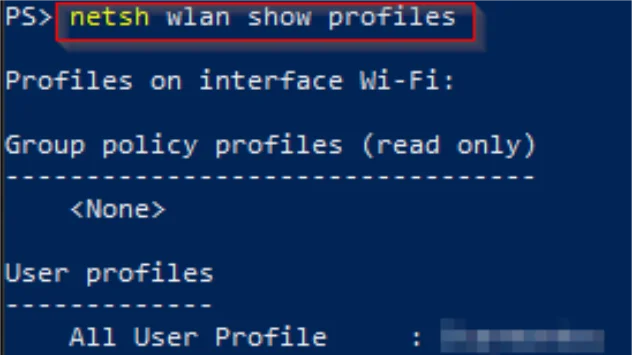
View Wireless Profile Password Information Using PowerShell or CMD
Training |
professionally evil |
Secure Ideas |
hacking |
Windows |
Windows 10 |
Windows 11 |
sysadmin |
system administration |
cmd |
wireless |
wifi |
wifi password |
powershell |
wireless profile
There are a couple different ways for you to access your Windows wireless password information. If ...
Continue Reading
What are the key requirements of the GLBA Safeguards Rule?
information security |
penetration testing |
CISSP |
education |
compliance |
risk assessment |
security controls |
information security program |
GLBA |
Safeguards Rule |
Dec 9, 2022 |
automotive |
banking |
vulnerability assessment
The Gramm-Leach-Bliley Act (GLBA) contains the Safeguards Rule. This requires financial businesses ...
Continue Reading
How to allow multiple RDP sessions
Training |
penetration testing |
pentesting |
Windows |
technology tips and tricks |
rdp |
sysadmin |
system administration
The goal of this article is to walk through how to set up a Windows host to allow multiple remote ...
Continue Reading
PowerShell Tips: How do I Mount a VHD or Lock a BitLocker Drive?
encryption |
security |
professionally evil |
Secure Ideas |
getting started |
BitLocker |
VHD |
rtfm |
manage-bde |
mount-vhd |
manage bitlocker |
technology |
technology tips and tricks |
Windows 10 |
VHDX |
encrypted drive |
technology tips |
how-to |
btfm |
Windows 11
PowerShell Tips How do I Mount a VHD or Lock a BitLocker Encrypted Drive?
Continue Reading
Boolean Math (NOT Logic) – CISSP Domain 3
Hello everyone. We’ve got another Boolean math session lined up for you today. This time we’re ...
Continue Reading
Boolean Math (XOR Logic) – CISSP Domain 3
Hello everyone. We’ve got another Boolean math session to look over today. Our focus this time will ...
Continue Reading
Boolean Math (OR Logic) – CISSP Domain 3
Today we are going to take another look at some Boolean mathematics. In particular, we’re going to ...
Continue Reading
Has contents: true
Total pages: 2
Current page: 1