Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
JuiceShop Workshop in less than 5 minutes
Training |
application security |
OWASP |
AWS |
IaC |
JuiceShop |
Containers |
AWS_ECS |
workshops |
Vagrant |
AWS-CDK
Have you ever deployed 10-30 containers in AWS with the single stroke of a key? (well if you don’t ...
Continue Reading
How to Obfuscate Strings in Rust the Easy Way Using the litcrypt Crate
Overview Static strings in a binary can make the life easier for reverse engineers, be those ...
Continue Reading
Application Security 202: Vulnerabilities Accepted
Testing |
Vulnerability |
Guidance |
data breach |
information security |
penetration testing |
application security |
professionally evil |
Secure Ideas |
hacking |
best practices |
cybersecurity |
Privilege Escalation
vul·ner·a·bil·i·ty The quality or state of being exposed to the possibility of being attacked or ...
Continue Reading
(Not So) Quick Bites - Episode 3 - Writing About Writer's Block
Deliverables |
consulting |
application security |
Secure Ideas |
cybersecurity |
methodology |
Project |
Writing |
Quick Bites
So, sometimes I have a real problem with writing, specifically reports and blog posts. Somehow, ...
Continue Reading
How to allow multiple RDP sessions
Training |
penetration testing |
pentesting |
Windows |
technology tips and tricks |
rdp |
sysadmin |
system administration
The goal of this article is to walk through how to set up a Windows host to allow multiple remote ...
Continue Reading
Hunting Secrets
Applications are hemorrhaging sensitive data. In many cases, the culprit is marketing and analytics ...
Continue Reading
Ensuring Web Security via Ansible (Apache)
NOTE: even though this will require Ansible, you can run this on any operating system contrary to ...
Continue Reading
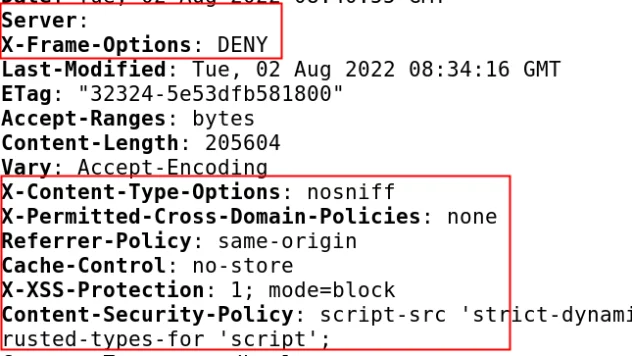
Why your application needs a Content Security Policy (And How to Build One)
As a web application owner, it is crucial to understand the concept of a content security policy ...
Continue Reading
Quick Bites Episode 2 - HTTP Security Headers and Why You NEED Them
Hi everybody! So, after some feedback about the last “quick” Quick Bites (thanks Josh!), I’ve ...
Continue Reading
Privilege Escalation via File Descriptors in Privileged Binaries
application security |
professionally evil |
Secure Ideas |
Linux |
programming |
File Descriptors |
SetUID |
Privilege Escalation
Today I wanted to cover an application security topic that applies to SetUID binaries. As we all ...
Continue Reading
Has contents: true
Total pages: 32
Current page: 13