Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
No Broadcast Traffic? No Problem! - NetExec SMB Slinky Module
As pentesters, tools such as Responder and Ntlmrelayx are great tools for capturing hashes or exploiting NTLM relay vulnerabilities. However, sometimes you may find yourself in a situation where there is no broadcast traffic on the subnet you are on that those tools can leverage. If there are ...
Continue Reading
Never miss a Professionally Evil update!
Running and Debugging Non-native ELF Binaries Locally Using QEMU, BINFMT, and GDB
Overview One of the common tasks that occurs when pentesting an embedded device is binary analysis ...
Continue Reading
Automating UART Command Injection with the Flipper Zero and JavaScript
Overview The Flipper Zero recently came out with a JavaScript system built off of MJS that exposes ...
Continue Reading
Flipper Zero: Hardware Hacking JTAG and SWD Webcast
The Flipper Zero is known as a hacking multitool. It can cover a range of hacking from sub-ghz ...
Continue Reading
SQL Injection Vulnerability: Identification and Prevention Methods
Recently, the FBI and CISA released a Secure by Design alert calling for the elimination of SQL ...
Continue Reading
Exploring Sentry Safe Exploit on the Flipper Zero with Logic Analyzer
hacking |
hardware |
flipper zero |
sentry |
safe |
logic analyzer
Overview I recently had a friend that wanted to learn how to use a logic analyzer. Given the number ...
Continue Reading
Flipper Zero: A Hardware Hacking Multitool Webcast
Training |
hacking |
hardware |
webcast |
flipper zero
The Flipper Zero is known as a hacking multitool. It can cover a range of hacking from sub-ghz ...
Continue Reading
Hardware Hacking: Interfacing to UART with Your Computer
In my previous article, we covered identification and mapping of the UART interface. In that ...
Continue Reading
Hardware Hacking: Finding UART Pinouts on PCBs
In my previous article, we started to explore the Universal Asynchronous Receiver/Transmitter ...
Continue Reading
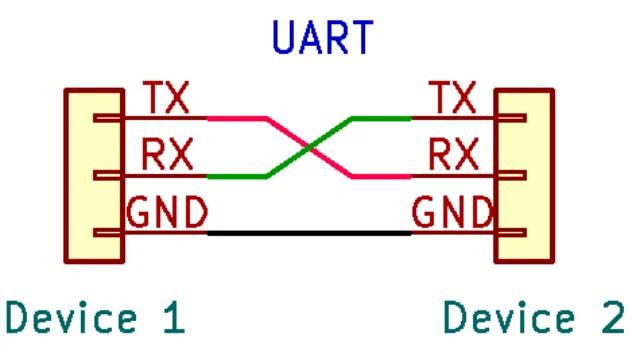
Hardware Hacking: Introduction to the UART Interface
I wanted to provide some information about hardware and firmware hacking in our blogs. To get the ...
Continue Reading
Introduction to Writing Nmap Scripting Engine (NSE) Scripts
NMAP |
programming |
NSE
One thing I notice a lot of people are missing in their skill set as security professionals is the ...
Continue Reading
Has contents: true
Total pages: 3
Current page: 1


%2c%20How%20to%20Identify%20Them%2c%20and%20How%20to%20Prevent.png)