Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
[Update] Using Components with Known Vulnerabilities
When an organization has a breach, you would like to imagine that the attacker crafted a new ...
Continue Reading
Kubernetes Security - A Useful Bash One-Liner
Whether you’re an administrator, pentester, devop engineer, programmer, or some other IT person, ...
Continue Reading
How I Became a Security Consultant: AbsoluteAppsec Interview
Every so often, podcasts and such will invite me to speak on a variety of topics. And this week, I ...
Continue Reading
Once upon a time there was a WebSocket
This is the story from one of our recent penetration testing engagements. Still, the story is a ...
Continue Reading
Building Blocks: Professionally Evil Fundamentals Series
We at Secure Ideas love security education. What we enjoy even more is affordable security ...
Continue Reading
It's Okay, We're All On the SameSite
With Google’s recent announcement that all cookies without a SameSite flag will be treated as ...
Continue Reading
In Case of Fire: Break Windows
When a client calls us to pentest a web application that is only available in Internet Explorer. I ...
Continue Reading
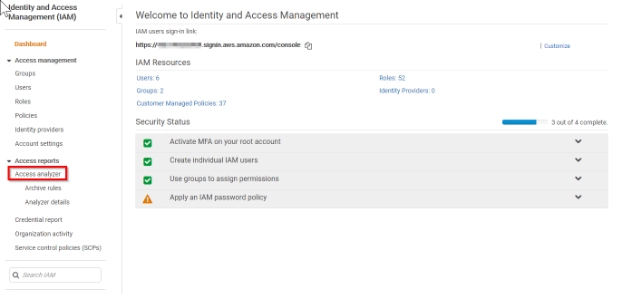
IAM Access Analyzer Review
TL;DR – This is a free tool that helps solve one of the biggest security problems when working in ...
Continue Reading
Security Review of Nest Camera
I love tinkering with home automation and security solutions. The simplicity of turning on a light ...
Continue Reading
IAM Root: AWS IAM Simulator Tutorial
If you needed yet another reason to be paranoid about your personal information being exposed, the ...
Continue Reading
My Experience in the CISSP Mentorship Program
A little while back, I was talking with a friend of mine about the different services that Secure ...
Continue Reading
Has contents: true
Total pages: 32
Current page: 18
![[Update] Using Components with Known Vulnerabilities](https://www.secureideas.com/hubfs/businessman%20hand%20showing%20partnership%20sign%20as%20%20concept.webp)