Frequently Asked Questions
Get the answers you need to choose the right security services for your organization.
4 Steps to prepare your application for a Denial of Service attack
When you hear the words "cyber attack," the first thing that comes to mind is probably ransomware ...
Continue Reading
What Tasks are Performed During a Hardware Security Assessment?
A hardware security assessment is a review of a physical device and a very common task when ...
Continue Reading
How is Embedded/IoT Scoping Different from a Normal Pentest?
consulting |
security |
penetration testing |
business |
scope |
IoT |
Embedded Device
A Penetration Test is a Penetration Test, Right? On the surface, that would be the case if we are ...
Continue Reading
Penetration Testing Compliance under GLBA in 2024 - What You Need to Know
information security |
penetration testing |
compliance |
risk assessment |
information security program |
GLBA |
Safeguards Rule |
vulnerability assessment
The Gramm-Leach-Bliley Act (GLBA) has established baseline privacy and cybersecurity standards for ...
Continue Reading
How Soon Can We Schedule a Test?
The short and sweet answer is that once a contract has been executed by both parties, and all ...
Continue Reading
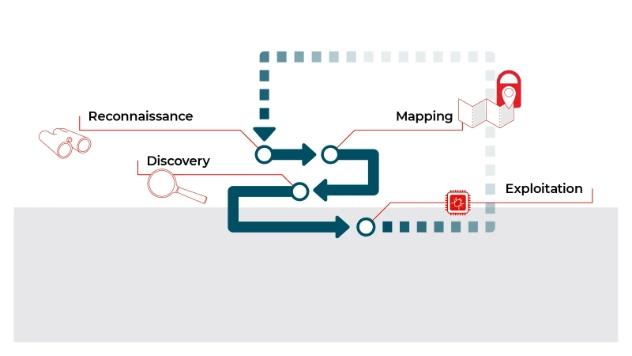
Secure Ideas' Penetration Testing Methodology
When it comes to partnering with an outside security consulting firm, there are many things to ...
Continue Reading
Project Responsibilities
consulting |
security |
web penetration testing |
information security |
penetration testing |
application security |
professionally evil |
Secure Ideas |
network security |
cybersecurity |
pentesting |
business |
service |
methodology |
Project |
Responsibilities
At Secure Ideas we pride ourselves on our attention to detail in preparing clients for a project. ...
Continue Reading
What Sets Secure Ideas Apart From Other Security Consulting Firms?
FAQ |
consulting |
security |
web penetration testing |
information security |
penetration testing |
professionally evil |
Secure Ideas |
network security |
cybersecurity |
pentesting |
business
Secure Ideas at a Glance As an industry leader in security consulting, training, and penetration ...
Continue Reading
Get To Know the Professionally Evil Experts
consulting |
information security |
penetration testing |
professionally evil |
Secure Ideas |
hacking |
cybersecurity |
pentesting |
technology |
industry leaders |
experts |
SME
Kevin Johnson - CEO, Principal Consultant, and Head Nerd!
Continue Reading
How to quickly estimate the cost of a penetration test.
If you are new to organizing a third-party penetration test, chances are you will face the ...
Continue Reading
What is a Gray Box Penetration Test?
The terms black box, white box, or gray-box are used to classify a type of penetration test in the ...
Continue Reading
Gray Box vs White Box vs Black Box
Every penetration test emulates an adversary to assess the security controls of the target systems. ...
Continue Reading
Has contents: true
Total pages: 7
Current page: 4