Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Looking for Malicious PHP Files
A while back I had to deal with a compromised web server for some folks. They had some WordPress ...
Continue Reading
Podcast Show Notes: Why are Passwords so Difficult
Kevin and James just finished up recording episode 2 of the Professionally Evil Perspective ...
Continue Reading
The Watering Hole: Is it Safe to Drink?
How many times have you been told you have a vulnerability that you just don’t understand its ...
Continue Reading
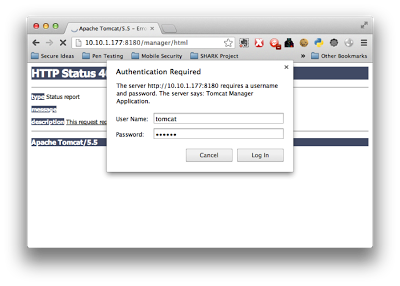
Admin Consoles, Default Creds, and Sweet Pwnage
When performing internal network penetration tests, one thing that really gets us excited is ...
Continue Reading
Decoding F5 Cookie
As a Penetration Tester, there are many different things you come across while performing a test. ...
Continue Reading
Introduction to MobiSec video
We just wanted to post a quick update to let you know about a new video. Kevin (working with James) ...
Continue Reading
Reading the Mandiant APT1 Report
Like a lot of folks, I downloaded and read through the Mandiant APT1 report as soon as I could. ...
Continue Reading
Active Defenses?
Active defense, often mistakenly called hacking back, is a common topic thrown around the security ...
Continue Reading
Grab a CORS Light
Many of you already know that any cross-site HTTP requests invoked from scripts running within a ...
Continue Reading
Laudanum by Example: Shell
Previously, I wrote a post providing a brief introduction to Laudanum. If you haven’t read it, or ...
Continue Reading
Introduction to Laudanum
As a security consultant, there are so many scenarios that I run into every day that there is no ...
Continue Reading
Has contents: true
Total pages: 32
Current page: 30