Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Is My Application Illegal?
Mobile devices and applications are everywhere. And we have seen tons of information, guides and ...
Continue Reading
Decoding Security Jargon
If you pick up just about any security textbook it will begin by describing security using terms ...
Continue Reading
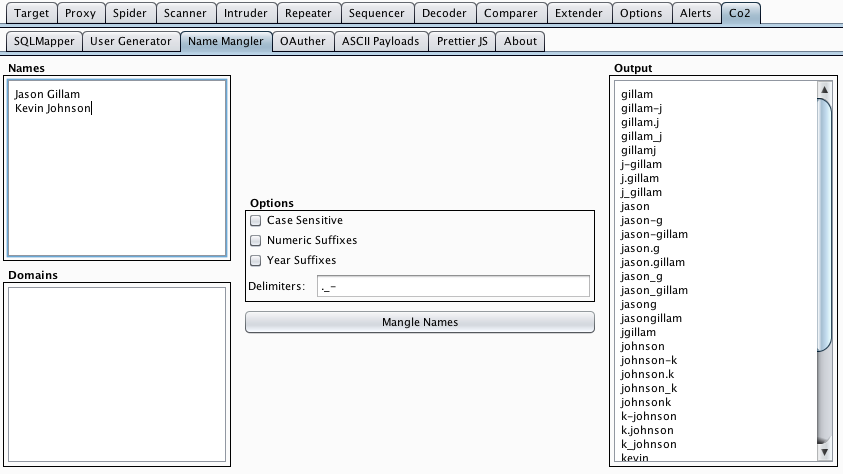
Burp Co2 Update v0.5 adds a Name Mangler module!
I’m excited to announce another addition to the Burp Co2 extension bundle in v0.5 of Burp Co2 ...
Continue Reading
Are we a Target?
2014 has started out with a bang in terms of publicly disclosed compromised systems. We entered the ...
Continue Reading
Scary Web Services: Part 2
This post may seem timely in light of the recent Snapchat compromise. Although Snapchat’s breach ...
Continue Reading
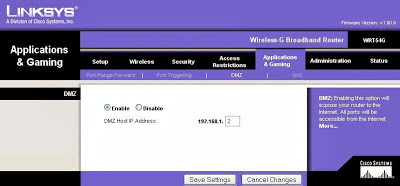
Intercepting DNS
Recently during a penetration test, I discovered a Linksys WRT54G wireless router that had been ...
Continue Reading
Professionally Evil Software: Laudanum 1.0 release!
Secure Ideas is excited to announce the immediate release of Laudanum 1.0. This open source project ...
Continue Reading
Why Target's Breach Included PIN Data
encryption |
PCI |
data breach |
target
Last Friday Target issued an update acknowledging that encrypted PIN data were included in the data ...
Continue Reading
Target Security Breached: What You Need to Know
All it takes is one big nasty security breach and the whole world will be watching you through a ...
Continue Reading
Password Sharing Across Accounts
Over the past few years we have seen a large number of databases get compromised leading to the ...
Continue Reading
Scary Web Services: Part 1
I have several things I want to say about web services but for this post I am going to constrain ...
Continue Reading
Has contents: true
Total pages: 32
Current page: 26