Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
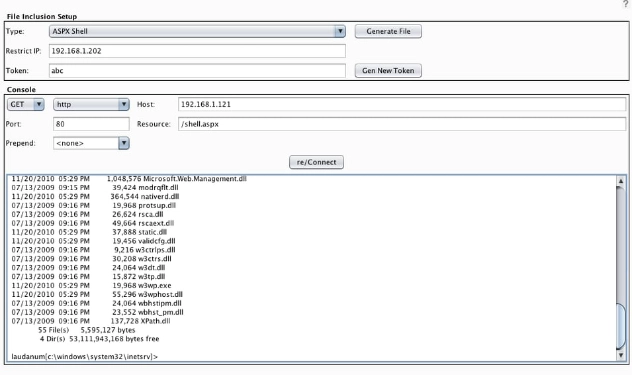
Burp CO2 now sports some Laudanum Scripts!
There have been a number of updates to the Burp CO2 extension suite over the past couple of months ...
Continue Reading
SQLite: the good, the bad, the embedded database
SQLite is an embedded, open-source, lightweight SQL database engine. The C based library is ...
Continue Reading
Thumb Drives.. Can you tell the difference?
During a physical penetration test, it is not uncommon for the tester (attacker) to drop usb thumb ...
Continue Reading
CORS Global Policy
I recently noticed an uptake on Cross-Origin Resource Sharing (CORS) findings showing up in ...
Continue Reading
The ABC's of ASV's & PCI
Secure Ideas prides itself on providing the highest level of service to our customers. We are ...
Continue Reading
Logging Like a Lumber Jack
Turn on any news outlet or visit any news site and you will most likely see an announcement of yet ...
Continue Reading
Policy Gap Analysis: Filling the Gaps
In today’s world, something never seems to be true unless it is written down, and even then it is a ...
Continue Reading
New Data Security Breach Laws in Florida
Since many organizations are collecting what many would consider personal, non-public, information, ...
Continue Reading
What Do You Expect From A PenTest?
There are many reasons that a company has a penetration test performed. Maybe it is due to ...
Continue Reading
Comprehensive Testing: Red and Blue Make Purple Video
James Jardine and I held the Comprehensive Testing (Purple Teaming) webcast yesterday. In this ...
Continue Reading
Purple Teaming for Success
You know what blue teams and red teams are. Red is our attack side, or the adversaries, and Blue is ...
Continue Reading
Has contents: true
Total pages: 32
Current page: 25