Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
We Can't Rely on the Browser for Protection
A large part of doing security consulting is providing proper mitigations and recommendations to ...
Continue Reading
Burp Extension for F5 Cookie Detection
This past February, my fellow colleague James Jardine wrote an excellent blog post called “Decoding ...
Continue Reading
Professionally Evil Perspective podcast: Mobile Security Testing - Tips and Tools
I have to say that I really enjoy doing the Professionally Evil Perspective (PEP) podcast with ...
Continue Reading
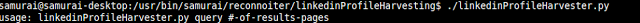
Professionally Evil Toolkit - Reconnoiter
In this series of the Professionally Evil Toolkit we will be talking about Reconnoiter. Reconnoiter ...
Continue Reading
Professionally Evil Toolkit - Sqlmap
In this series of the Professionally Evil Toolkit we will be talking about sqlmap. Sqlmap is an ...
Continue Reading
Your Passwords Were Stolen: What's Your Plan?
If you have been glancing at many news stories this year, you have certainly seen the large number ...
Continue Reading
Using a Throwing Star to Capture Packets
Mobile applications are a hot commodity these days. It seems like everyone and their brother/sister ...
Continue Reading
Brute Forcing the Change Password Feature
As a penetration tester, brute force attacks are something I test for on every application. ...
Continue Reading
GSA Database May Have Leaked Information: Kevin Johnson was Interviewed
Recently it was announced that there was a security flaw found in one of the GSA systems that could ...
Continue Reading
Podcast Show Notes: Why are Passwords so Difficult
Kevin and James just finished up recording episode 2 of the Professionally Evil Perspective ...
Continue Reading
The Watering Hole: Is it Safe to Drink?
How many times have you been told you have a vulnerability that you just don’t understand its ...
Continue Reading
Has contents: true
Total pages: 5
Current page: 3