When it comes to partnering with an outside security consulting firm, there are many things to consider to ensure they truly understand the challenges you are facing, and possess the capacity to meet your organization’s needs such as:
- Have they worked with companies of similar size and industry?
- How long have they been offering the services you are looking for?
- Do they possess the skills and expertise, as well as a proven track record of high performance they can validate?
- Do they follow an industry standard testing methodology that produces results, actionable recommendations, and insights that will guide your organization into the future?
These are all questions you should be asking yourself if you are in the market for a third party consulting firm like Secure Ideas. We make every effort to be as transparent as possible, and provide the answers you are looking for, so as fortune would have it, if you’re reading this article we’re confident you’ve come to the right place.
In this specific write-up we will focus on the final question regarding testing methodology. If after reading this you have other questions, please feel free to peruse our Knowledge Center for more answers from the Professionally Evil team.
Looking for our Methodology? Look No Further!
Download a copy of our detailed penetration testing methodology here!
Not all testing methodologies are created equal, and many dubious consulting firms do not follow recognized industry standards. That is not to say you should by default be skeptical, but it is important to review a company’s processes to determine whether or not they align with your needs, and if you’re not certain, don’t hesitate to request clarification. After all, if they aren’t willing or able to entertain your inquiry, chances are pretty good they aren’t the right fit for you.
So What’s in Our Methodology?
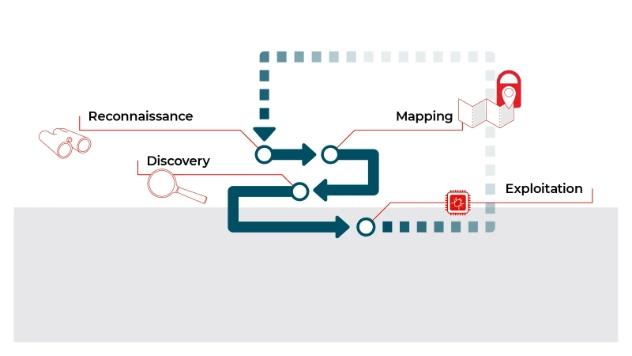
Secure Ideas follows an industry standard testing methodology, consisting of a four-step process as follows:
- Reconnaissance - We will search public sources for information regarding your organization’s infrastructure, systems, and applications.
- Mapping - During this stage of a pentest, we will study the systems and services provided by your organization.
- Discovery - Information that is gathered during the previous two steps will be used to assist our consultants in finding vulnerabilities.
- Exploitation - Through exploitation we are able to provide a realistic understanding of the business exposure to your organization, and rather than simply stating that a vulnerability exists, our consultants will attempt to determine the actual risk said vulnerability presents.
If you have any questions, or would like to review our other industry standard methodologies, please refer to the following list.
Red team and penetration testing
It is critical that your organization performs their due diligence during the vetting process, so if you’re currently engaging with a consulting firm who is reluctant to provide the information you’re in search of, that should certainly raise a red flag. If this is the case for you, please contact us. We’d be pleased to have the opportunity to answer your questions as we endeavor to offer you the best pentesting experience possible.