Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
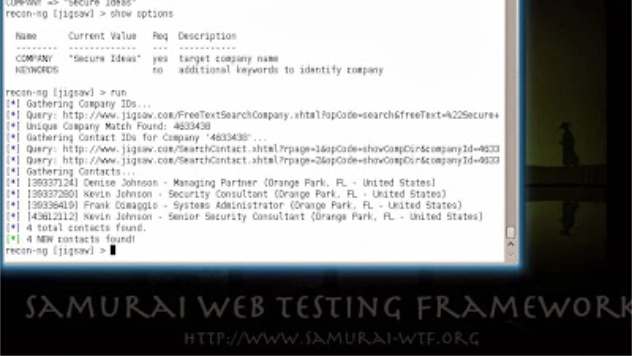
Professionally Evil Toolkit - Recon-ng
The first stage of almost every successful penetration test is the reconnaissance phase. During ...
Continue Reading
Security Tubthumping
I have a friend who is an alcoholic. A few weeks ago after 5 years of sobriety, she stumbled and ...
Continue Reading
Comparing Authorization Levels with Burp's Compare Site Map feature
Burp Suite from Portswigger.net is a fantastic web app testing tool that we use regularly at Secure ...
Continue Reading
Defending Against Pass-the-Hash (PtH) Attacks
Pass-the-Hash (PtH) attacks have become probably the most common form of credential attacks used in ...
Continue Reading
Kismet Log Viewer v2 Tool Released
Secure Ideas actively supports open source and giving back to the community. In that light, we’re ...
Continue Reading
Getting Started with BeEF: The Browser Exploitation Framework
BeEF, the Browser Exploitation Framework, is a testing tool designed to enable penetration testers ...
Continue Reading
Preparing for a Consultant
As security consultants, we regularly travel to clients’ sites and experience a wide range of ...
Continue Reading
Has contents: true
Total pages: 2
Current page: 2