Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
What does PCI require for Developer Training?
The Payment Card Industry Security Standards Council (PCI SSC) defines compliance standards for all organizations that accept credit card payments. These standards cover a wide range of technologies and situations that impact the security of credit card transactions. The Data Security Standard ...
Continue Reading
Never miss a Professionally Evil update!
Everything You Need To Know About The Nist Cybersecurity Framework 2.0
best practices |
cybersecurity |
government |
CSF |
cybersecurity standards |
framework |
NIST |
profiles |
tiers
This week NIST released the highly anticipated update to the Cybersecurity Framework (CSF). Here’s ...
Continue Reading
Asset Discovery
The first step in securing any organization is to understand what you have. Unless you have a ...
Continue Reading
10 Tips for Engaging a Security Services Vendor
The Information Security market brought in an estimated $167 billion in 2019 and that’s expected to ...
Continue Reading
How to Test Your Security Controls for Small/Medium Businesses
We often get contacted by small businesses requesting their first penetration test because of ...
Continue Reading
Compliance is not Security
Many folks get confused about the difference between security and compliance. Many, especially ...
Continue Reading
Silencing Firefox's Chattiness for Web App Testing
Firefox is one chatty browser! Even if you don’t actually use it for anything, it’s constantly ...
Continue Reading
These Aren't the Password Guidelines You're Looking For
“You don’t need to see his identification.” It’s a classic line. With a flick of the wrist old Ben ...
Continue Reading
Protecting your Kids from Online Threats
“The greatest gifts you can give your children are the roots of responsibility and the wings of ...
Continue Reading
We're Just Like the NSA, and Nothing Like Them
During penetration tests, and especially scoping calls, we often get quizzed about what secret, ...
Continue Reading
Introduction to Metasploit Video
The Metasploit Framework is a key resource for security assessors. Whether you’re goal is to become ...
Continue Reading
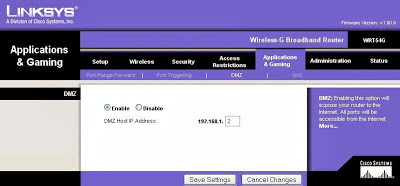
Intercepting DNS
Recently during a penetration test, I discovered a Linksys WRT54G wireless router that had been ...
Continue Reading
Has contents: true
Total pages: 2
Current page: 1
.png)