Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Red Teaming - Not What You May Have Thought
Lately, I’ve been doing a lot of reading on some less technical topics and I ran across “Red Team: How to Succeed By Thinking Like the Enemy” by Micah Zenko. If you are like me, you’ve probably thought of the red team as being a penetration test group or some kind of adversary simulation. You know, ...
Continue Reading
Never miss a Professionally Evil update!
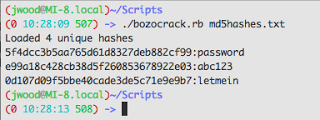
Professionally Evil Toolkit - BozoCrack
This week I’ve been teaching a class on web app security for developers and I remembered a fun ...
Continue Reading
Why Do Phishing As Part of Security Testing
I was recently watching a web cast on incident response and found myself thinking about the cause ...
Continue Reading
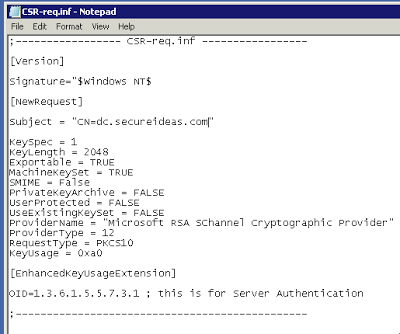
Creating SSL Certificate Requests Using Certreq.exe and Enable LDAPS
This post picks up on my last about creating and authorizing an internal certificate authority. We ...
Continue Reading
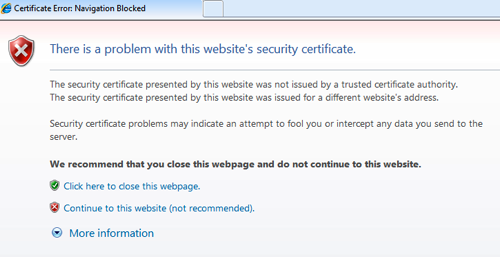
SSL Certificates: Setting Up and Authorizing the Internal Certificate Authority
In this post, I wanted to give something directly to the Blue Teams out there. I also thought I ...
Continue Reading
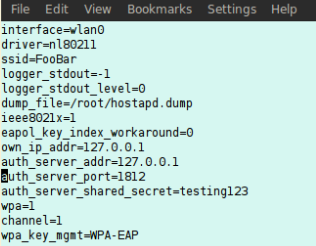
Professionally Evil: This is NOT the Wireless Access Point You are Looking For
I was recently conducting a wireless penetration test and was somewhat disappointed (but happy for ...
Continue Reading
Looking for Malicious PHP Files
A while back I had to deal with a compromised web server for some folks. They had some WordPress ...
Continue Reading
Reading the Mandiant APT1 Report
Like a lot of folks, I downloaded and read through the Mandiant APT1 report as soon as I could. ...
Continue Reading
Hi, I'm with IT and I'm Here to Steal From You
Beware of the Unknown IT Grunt I decided to continue on with the same theme as Kevin’s post about ...
Continue Reading
Has contents: true
Total pages: 1
Current page: 1