Professionally Evil Insights
Welcome to the Professionally Evil Insights blog by Secure Ideas! In this digital playground, we unravel the complex world of information security with a touch of fun. Our expert-led content ranges from deep-dives into penetration testing to explorations of hardware hacking. Whether you're curious about Secure Ideas or passionate about cybersecurity, this blog is your quick, enlightening, and entertaining guide into the captivating world of information security.
Welcome aboard!
Are You Ready for Your Pen Test?
It is day three of a five-day penetration test engagement and we still don’t have all the ...
Continue Reading
Five Outdated Security Excuses
The Security Industry as a whole has been known to criticize businesses large and small with ...
Continue Reading
Introducing Burp Correlator!
This one is for you web penetration testers! This new Burp extension is designed to help with ...
Continue Reading
Practical Pentest Advice from PCI
The PCI Security Standards Council released a Penetration Testing Guidance information supplement ...
Continue Reading
Tip: Running BurpSuite on a Mac
Here’s a quick tip I use to save some time when spinning up Burp Suite on a Mac. I use Burp Suite ...
Continue Reading
Don't Forget the Little Things!
On January 31st, Deusen disclosed what was described as a Same Origin Policy Bypass flaw called ...
Continue Reading
CarolinaCon 11 Slides for Anatomy of Web Client Attack
For those who have asked – my slide deck for Anatomy of Web Client Attacks can be downloaded here. ...
Continue Reading
Adventures in LDAP Injection: Exploiting and Fixing
Every pen tester looks forward to that next encounter that includes one of those uncommon ...
Continue Reading
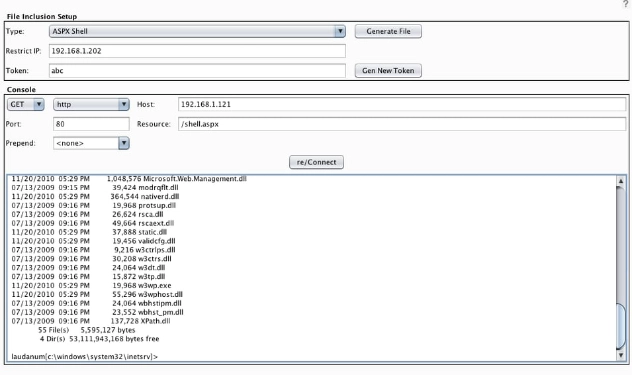
Burp CO2 now sports some Laudanum Scripts!
There have been a number of updates to the Burp CO2 extension suite over the past couple of months ...
Continue Reading
CORS Global Policy
I recently noticed an uptake on Cross-Origin Resource Sharing (CORS) findings showing up in ...
Continue Reading
Decoding Security Jargon
If you pick up just about any security textbook it will begin by describing security using terms ...
Continue Reading
Has contents: true
Total pages: 3
Current page: 2