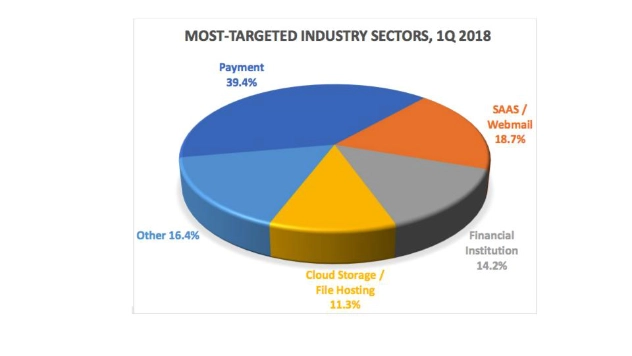
- The online payment sector was targeted by phishing more than in any other industry sector
- Phishers continue to fool Internet users into complacency by using HTTPS protection on phishing sites
- By Q2 of 2018, more than a third of phishing attacks were hosted on Web sites that had HTTPS with valid certificates
- Phishers are generally using domain names in the largest top-level domains and at the largest registrars
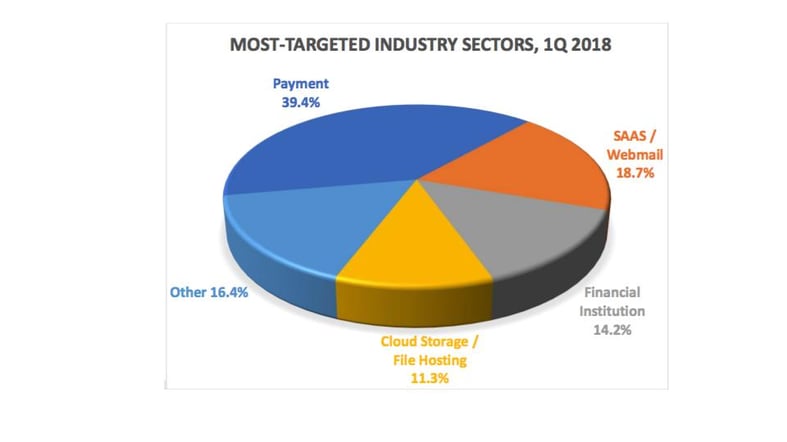
Phishing Activity Trends Report, 1st Quarter 2018. www.apwg.org
Phishing emails are designed to gain attention and typically contain a call to action. Employing both social engineering and technical subterfuge, phishing attacks allow criminals to steal consumers’ personal identity data and financial account credentials, among other sensitive information. As demonstrated above, financial information proves to be a significant target for a phisher, but still accounts for roughly half of the attacks on the Internet so far in 2018. According to Cloudmark’s Spear Phishing: The Secret Weapon Behind the Worst Cyber Attacks, the average phishing attack costs a mid-size company about $1.6 million, which can be financially devastating. Additionally, according to the FBI, phishing scams alone cost businesses over $5 billion from 2013 to 2016.
What to look for?
- Any request via email to move to a separate site and input credentials. FULL STOP. Phishers will use well known logos and spoofed email addresses to appear as legitimate as possible. Any request for credentials should be a cause for alarm.
- Emails coming in the form of a help desk support ticket or a message from your bank.
- Calls to action – any email requiring time sensitive input of credentials should be cause for scrutiny.
What can be done?
- Increase employee security awareness – this includes not simply training your employees, but submitting them to regular assessments to gauge attention to detail and susceptibility to attack. October is National Cyber Security Awareness month. This is a problem. Educating your people should not be a checkbox once a year. It needs to be consistent.
- No fear reporting – Users should also be trained to let their security team know when they do make mistakes. Fear of punishment, rather than embracing the opportunity for education, does not assist an organization in identifying a compromise from a user.
- Utilize a password manager – A strong password management solution uses auto-login and auto-fill technology to analyze a webpage before filling in a user’s sensitive information. Criminals using spoofed domains, will not succeed when a password manager is there to recognize the URL, preventing auto-login. A password management system also discourages the use of duplicated passwords, thus limiting the attack surface for a criminal.
- Multi-Factor Authentication – MFA is a security system that requires more than one method of authentication from independent categories of credentials to verify a user’s identity for a login or other sort of transaction. Enabling Multi-Factor Authentication on online payment applications and any application containing possibly sensitive information is another layer of security that prevents attackers from using credentials to directly access an application.