As a consultant for Secure Ideas there are many tools I use often in my daily tasks. One of the many great tools I use in web application testing is Burp Suite.
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities (‘https://portswigger.net/burp/’). You may download it for free at http://portswigger.net.
During this demonstration I will be using a Virtual Machine of SamuraiWTF. The Samurai Web Testing Framework is a virtual machine, supported on VirtualBox and VMWare, that has been pre-configured to function as a web pen-testing and training environment. The VM contains the best of the open source and free tools that focus on testing and attacking websites. SamuraiWTF can be downloaded free of charge from https://sourceforge.net/projects/samurai/.
Be very mindful that if you start testing a web site without prior approval from the owner you could get yourself into a lot of trouble. It’s kind of like going to your neighbor’s house sitting down at their kitchen table and having breakfast while they are still in bed on a Sunday morning.
Burp can require a lot of memory resources while testing. I normally launch Burp by typing the following command at the command prompt:
‘java -Xmx4096m -jar {location of Burp jar file}’. You can also select the application under Samurai/Mapping/Interception Proxies/Burp Suite in Samurai WTF VM. Keep in mind that the Xmx option is setting the Java heap size, so if you have less than 8GB of memory, setting this to 4096M is probably not a good idea. 😉 For tips on setting up a Burp Automator script on your Mac, see our blog post on the topic.
If you have never installed Burp and are unfamiliar with the settings please refer to https://portswigger.net/burp/help/suite_gettingstarted.html to get it configured and set up for use. Once launched select next and then start using Burp default settings then hit next and ensure intercept is off under the Proxy Tab.
After you have Burp launched you may notice there are many tabs and features in Burp that serve different functions. The one tab we will discuss is the Repeater tab. We will cover the others in further posts or you can join the web class on Burp Suite at http://www.secureideastraining.com. Burp Repeater is a tool for manually modifying, reissuing individual HTTP requests, and analyzing their responses. During our web penetration tests and our WebScout testing services, we use Repeater quite frequently as a method to manipulate various parameters within the application. This allows us to manually test applications to discover a variety of flaws. Especially with modern applications, this is a very important method for testing the security of the application.
Now let’s get to testing. First, we need to pick a web site and start mapping out the site. I am using Firefox with Foxyproxy enabled and Burp Suite as my proxy on the Samurai WTF VM.
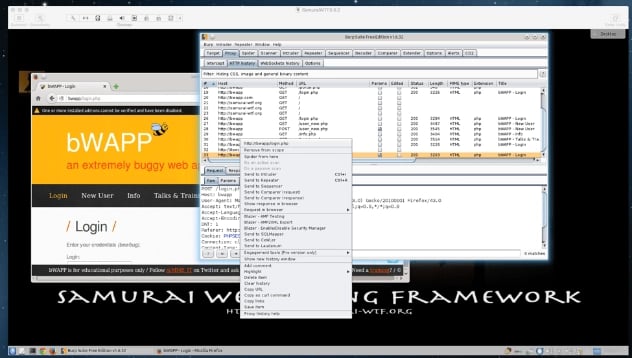
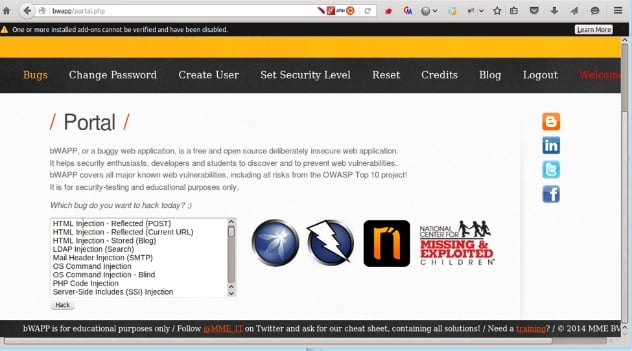
For this blog we are going to use bWAPP which is an intentionally buggy web application. In Firefox navigate to http://bwapp/login.php, then log into bWAPP using bee/bug as the login. Start mapping out your site, by selecting all the different tabs throughout your application.
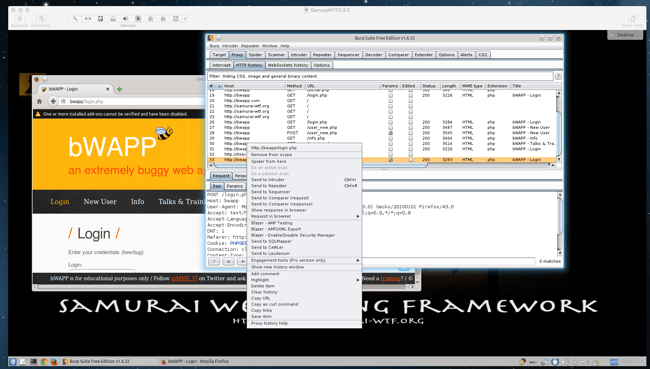
In Burp under the Target tab right click on http://bwapp and add to scope. By adding your target site to the scope, this will weed out any superfluous websites and keep your testing focused on what is in scope.
One item I found while mapping the bWAPP site was an OS Command Injection hack. This can be found under the bug list when logged in to bWAPP.
I typed in my web site I wanted to lookup and then searched for the results in Burp. Now I select the last entry in Burp’s Proxy tab which is where I performed the lookup and send that to Repeater by right clicking on the entry listed.
Select the Repeater tab and then select Go, this will give you the current state of your page before anything is altered to give us a reference point. This verifies the session is still active and the page does not block any replay of the request. We want to compare what comes back in Repeater to what we received in our original request from the browser to make sure nothing has changed.
Now once the target parameter is sent to Repeater and we can manipulate the cookies login/password or any other interesting items in order to send this to other tools such as intruder, decoder or comparer. These tools will be discussed in a later blog.
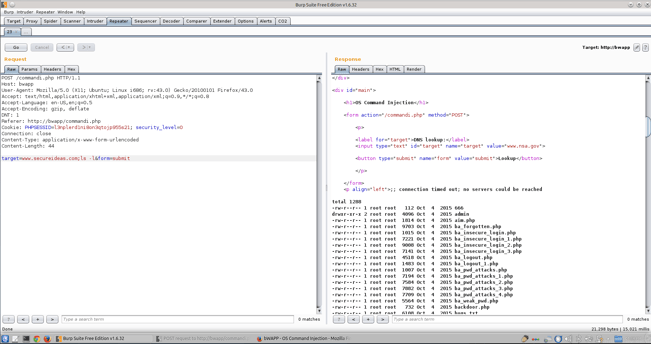
So let’s play around with this and see what happens when we add some things to the target field with “target=www.secureideas.com;ls -l” and select Go. We can look at the results and see what was returned.
Notice that we returned a directory file list of the website. Now let’s dig a little further and change our target to “target=www.secureideas.com;cat /etc/passwd” and rerun the test.
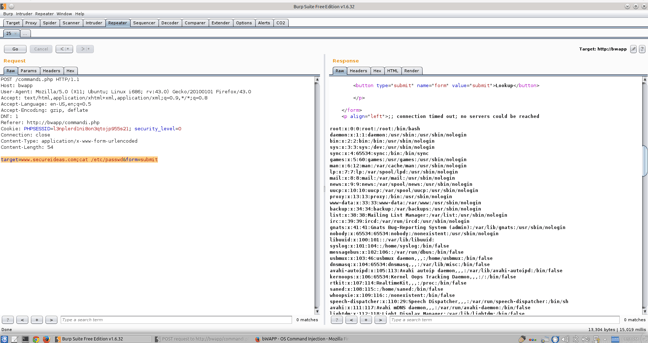
So using Repeater, we have discovered a Command Injection flaw within the application. We can then take this information and pivot deeper into the server or the network we are targeting. So that is basically it for Burp Repeater. It’s all about playing with different fields on the page and see what can be changed or manipulated to get a different result than intended?
In the next segment I will explore the Intruder tab another resourceful tool in Burp Suite which can be used to help in a Brute Force attack. If you would like a more in depth tutorial on Burp please sign up for the Tactical Burp recorded class on the Secure Ideas web site at http://www.secureideastraining.com/courses. If you have any questions or comments on my blog, feel free to reach out to us at https://www.secureideas.com or email me at larry@secureideas.com.